This is my TryHackMe walkthrough, created to document my learning journey and share solutions with the community. The writeups include a mix of hints, step-by-step explanations, and final answers to help players who get stuck, while still encouraging independent problem-solving.
Detecting Web Attacks Room - Explore web attacks and detection methods through log and network traffic analysis.
Overview
- Room URL: https://tryhackme.com/room/detectingwebattacks
- Difficulty: Easy
- Time to complete: 60
Walkthrough
1. Introduction
No hints needed!
2. Client-Side Attacks
What class of attacks relies on exploiting the user's behavior or device?
=> Answer: Client-Side
What is the most common client-side attack?
=> Answer: XSS
3. Server-Side Attacks
What class of attacks relies on exploiting vulnerabilities within web servers?
=> Answer: Server-Side
Which server-side attack lets attackers abuse forms to dump database contents?
=> Answer: SQLi
4. Log-Based Detection
What is the attacker's User-Agent while performing the directory fuzz?
cd Desktop
cat access.log
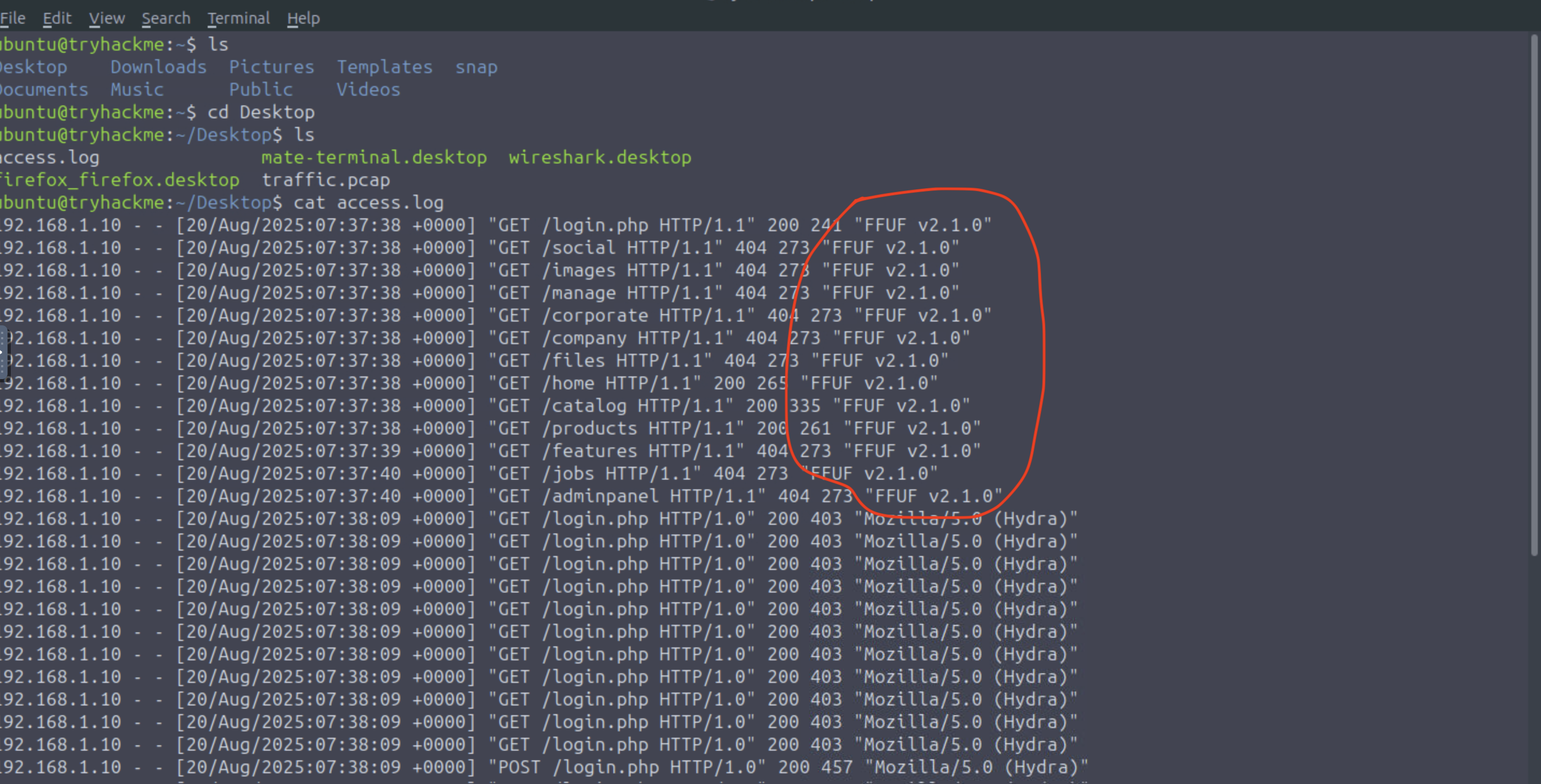
=> Answer: FFUF v2.1.0
What is the name of the page on which the attacker performs a brute-force attack?
=> Answer: login.php
What is the complete, decoded SQLi payload the attacker uses on the
/changeusername.phpform?
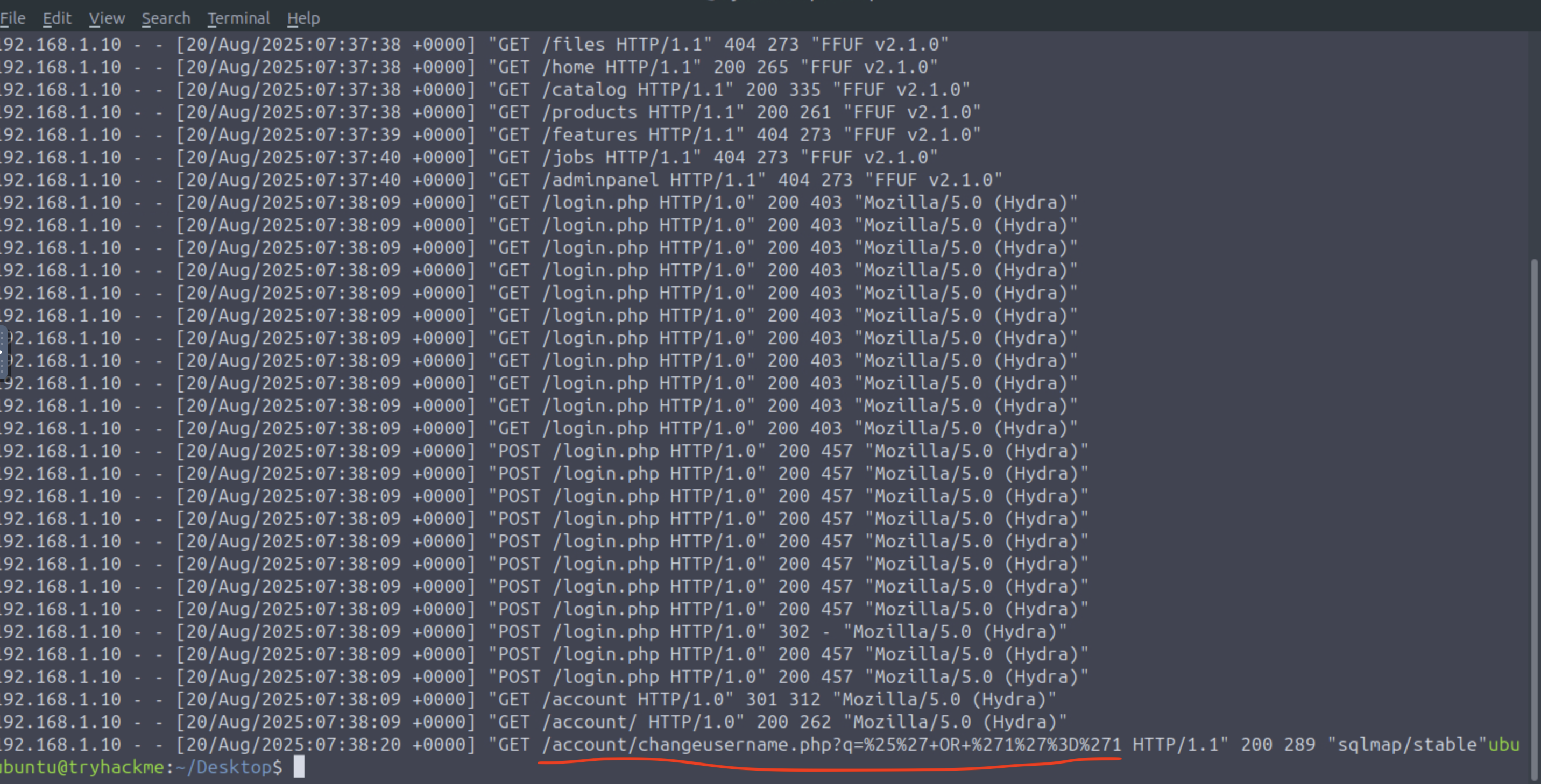
- Copy the
qquery value to URL Decode
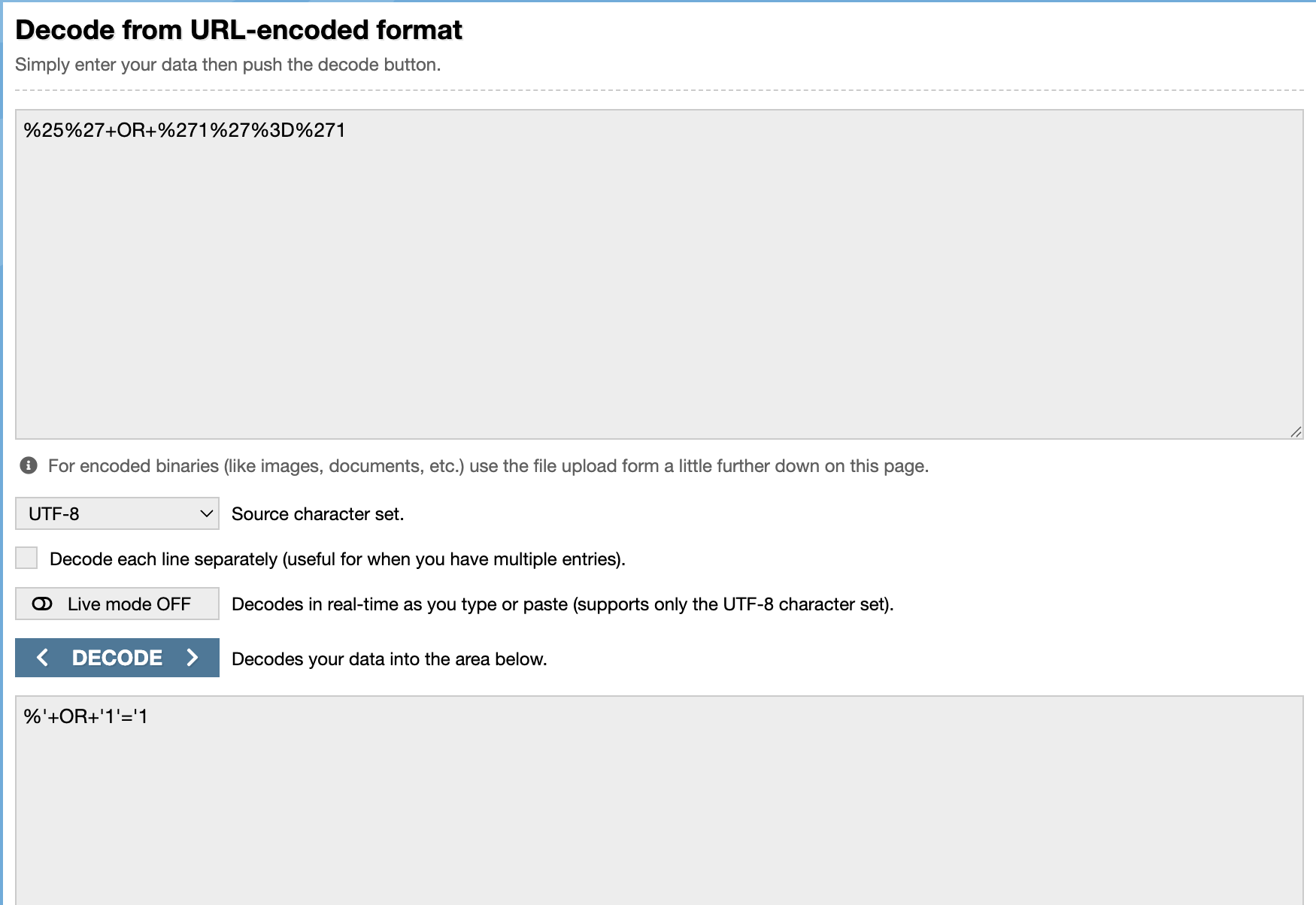
=> Answer: %' OR '1'='1
5. Network-Based Detection
What password does the attacker successfully identify in the brute-force attack?
wireshark ./traffic.pcap
- Apply filter
http.request.method == "POST"
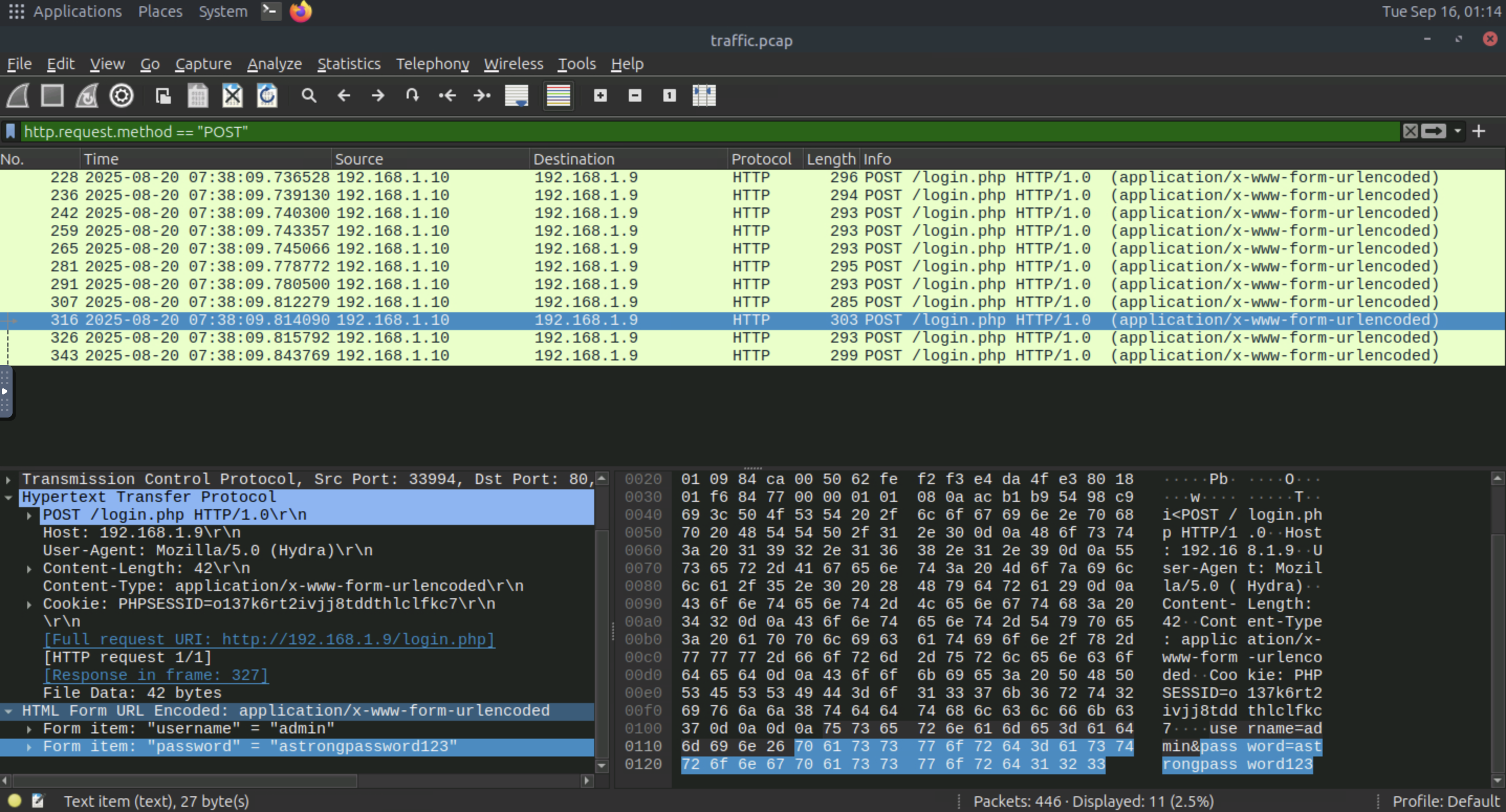
=> Answer: astrongpassword123
What is the flag the attacker found in the database using SQLi?
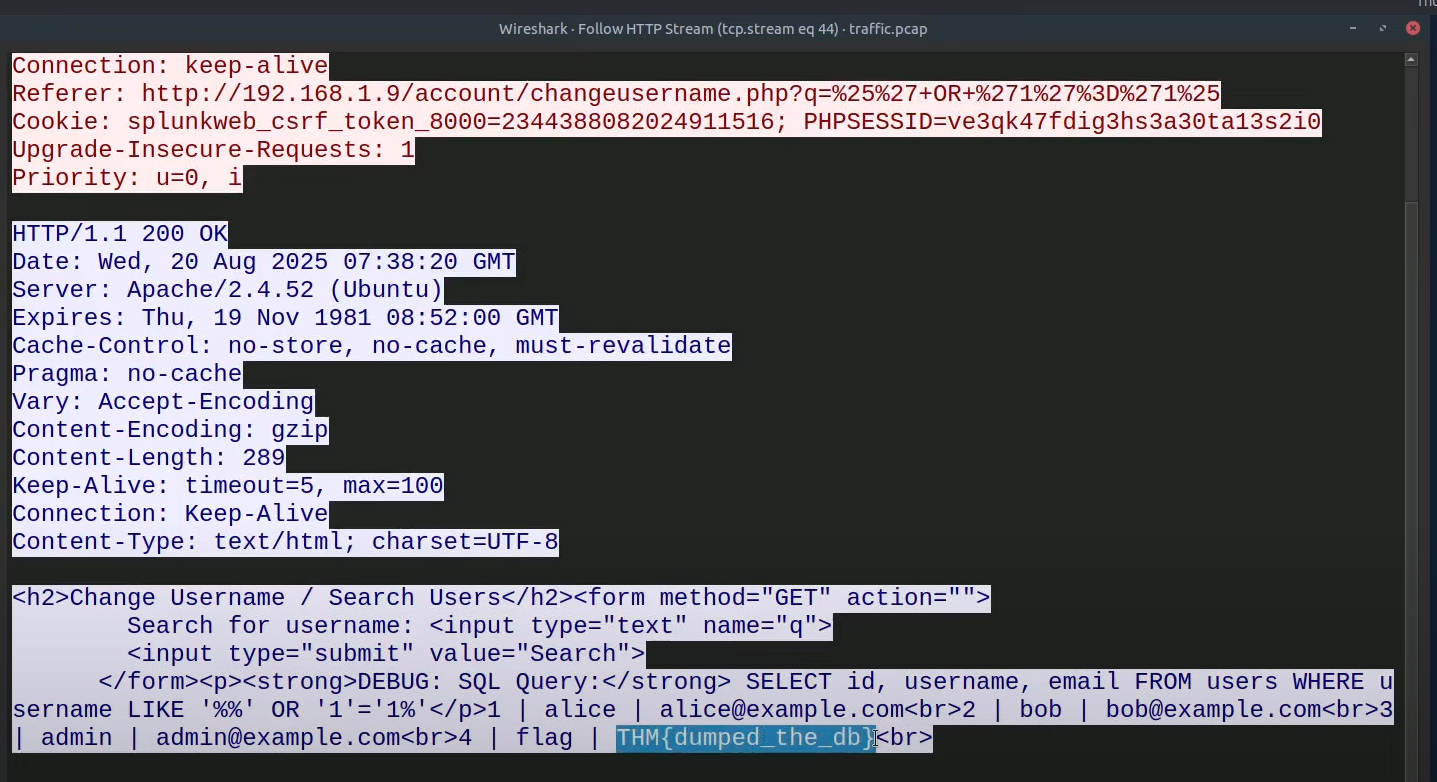
=> Answer: THM{dumped_the_db}
6. Web Application Firewall
What do WAFs inspect and filter?
=> Answer: Web Requests
Create a custom firewall rule to block any
User-Agentthat matches"BotTHM".
=> Answer: IF User-Agent CONTAINS "BotTHM" THEN block
7. Conclusion
No hints needed!