This is my TryHackMe walkthrough, created to document my learning journey and share solutions with the community. The writeups include a mix of hints, step-by-step explanations, and final answers to help players who get stuck, while still encouraging independent problem-solving.
Kenobi Room - Walkthrough on exploiting a Linux machine. Enumerate Samba for shares, manipulate a vulnerable version of proftpd and escalate your privileges with path variable manipulation.
Overview
- Room URL: https://tryhackme.com/room/kenobi
- Difficulty: Easy
- Time to complete: 45
Walkthrough
1. Deploy the vulnerable machine
Scan the machine with nmap, how many ports are open?
nmap <MACHINE_IP> -vvv
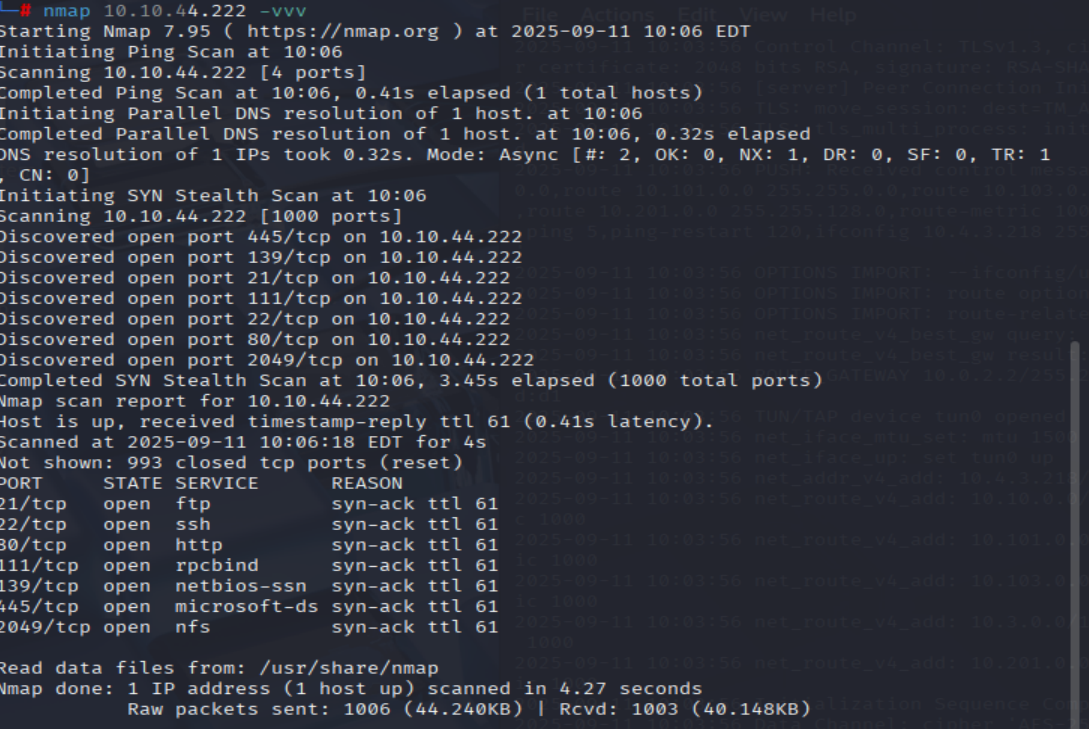 => Answer:
=> Answer: 7
2. Enumerating Samba for shares
Using nmap we can enumerate a machine for SMB shares.
Nmap has the ability to run to automate a wide variety of networking tasks. There is a script to enumerate shares!
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse MACHINE_IP
SMB has two ports, 445 and 139.

Using the nmap command above, how many shares have been found?
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.44.222
# or
smbclient -L //<MACHINE_IP>/ -N
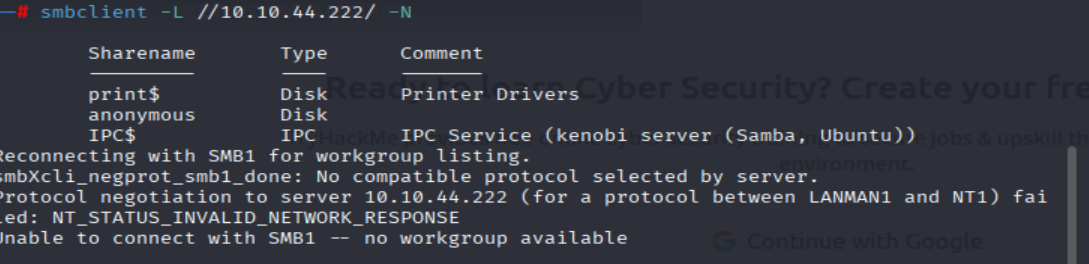
=> Answer: 3
On most distributions of Linux smbclient is already installed. Lets inspect one of the shares.
smbclient //MACHINE_IP/anonymous
Using your machine, connect to the machines network share.

Once you're connected, list the files on the share. What is the file can you see?
smbclient //<MACHINE_IP>/anonymous
smb: \> ls
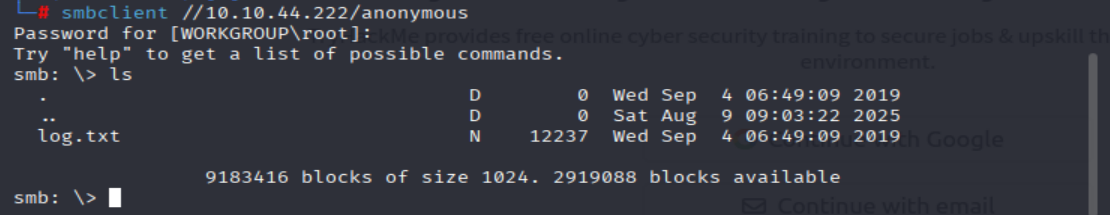
=> Answer: log.txt
You can recursively download the SMB share too. Submit the username and password as nothing.
smbget -R smb://MACHINE_IP/anonymous
Open the file on the share. There is a few interesting things found.
- Information generated for Kenobi when generating an SSH key for the user
- Information about the ProFTPD server.
What port is FTP running on?
nmap <MACHINE_IP>

=> Answer: 21
Your earlier nmap port scan will have shown port 111 running the service rpcbind. This is just a server that converts remote procedure call (RPC) program number into universal addresses. When an RPC service is started, it tells rpcbind the address at which it is listening and the RPC program number its prepared to serve.
In our case, port 111 is access to a network file system. Lets use nmap to enumerate this.
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount MACHINE_IP
What mount can we see?
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount <MACHINE_IP>
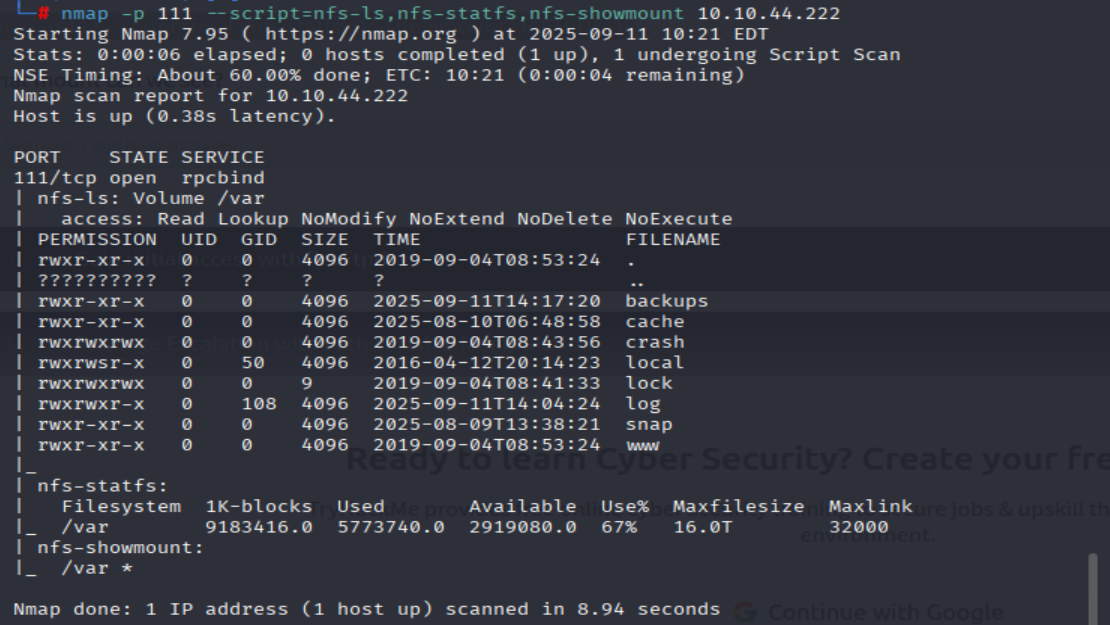
=> Answer: /var
3. Gain initial access with ProFtpd
Lets get the version of ProFtpd. Use netcat to connect to the machine on the FTP port.
What is the version?
netcat <MACHINE_IP> 21
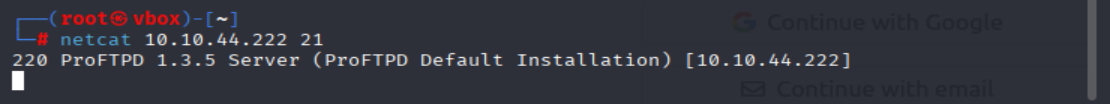
=> Answer: 1.3.5
We can use searchsploit to find exploits for a particular software version.
Searchsploit is basically just a command line search tool for exploit-db.com.
How many exploits are there for the ProFTPd running?
searchsploit ProFTPd 1.3.5
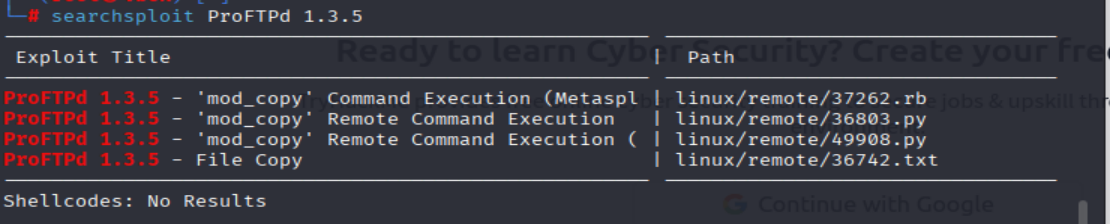
=> Answer: 4
Lets mount the /var/tmp directory to our machine
mkdir /mnt/kenobiNFS
mount MACHINE_IP:/var /mnt/kenobiNFS
ls -la /mnt/kenobiNFS
We now have a network mount on our deployed machine! We can go to /var/tmp and get the private key then login to Kenobi's account.

What is Kenobi's user flag (/home/kenobi/user.txt)?
# follow the above steps
cat /home/kenobi/user.txt
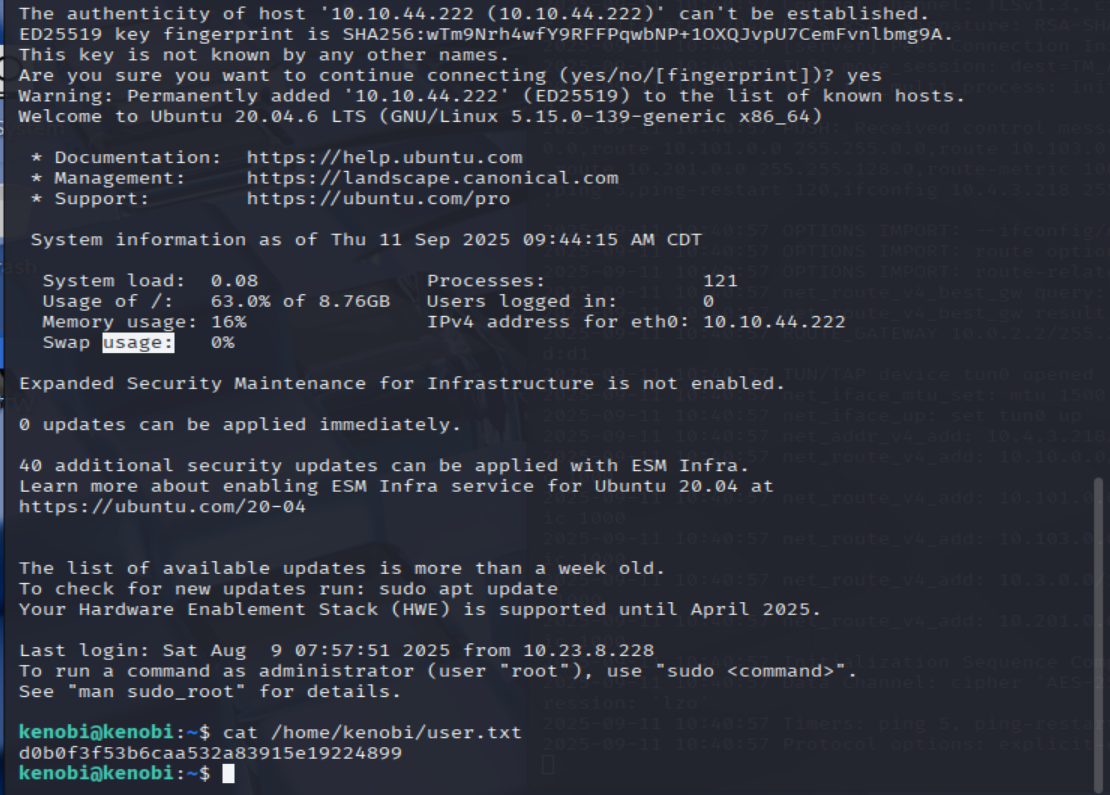
=> Answer: d0b0f3f53b6caa532a83915e19224899
4. Privilege Escalation with Path Variable Manipulation
SUID bits can be dangerous, some binaries such as passwd need to be run with elevated privileges (as its resetting your password on the system), however other custom files could that have the SUID bit can lead to all sorts of issues.
To search the a system for these type of files run the following: find / -perm -u=s -type f 2>/dev/null
What file looks particularly out of the ordinary?
find / -perm -u=s -type f 2>/dev/null
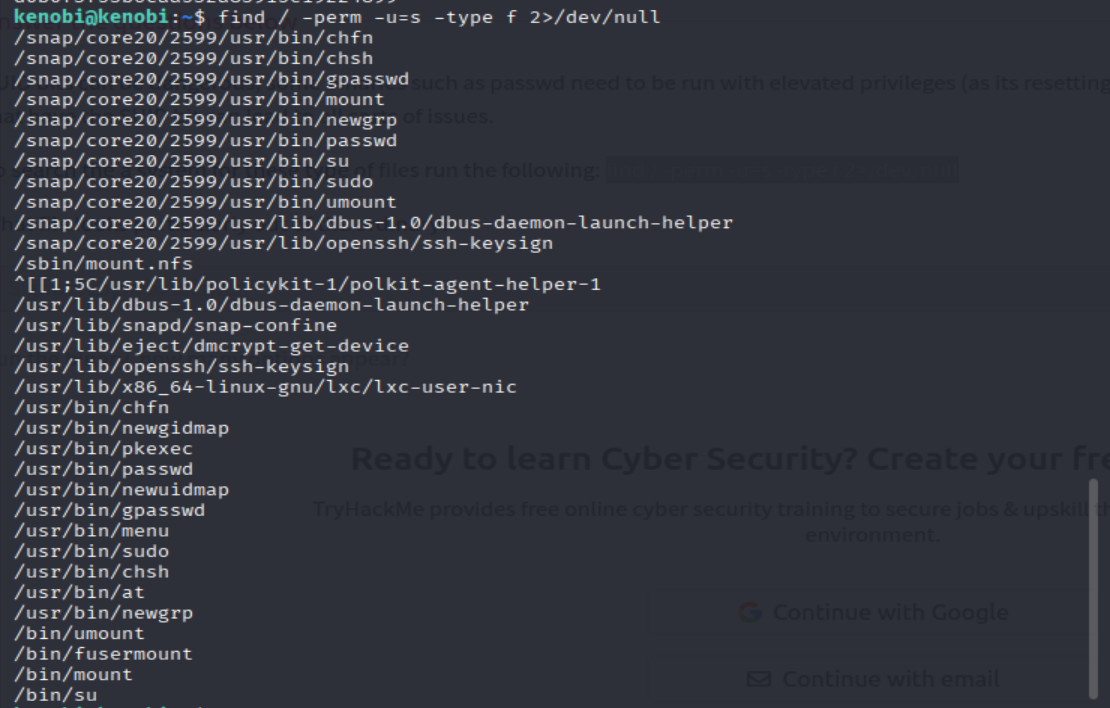
=> Answer: /usr/bin/menu
Run the binary, how many options appear?
menu

=> Answer: 3
What is the root flag (/root/root.txt)?
=> Answer: 177b3cd8562289f37382721c28381f02
