This is my TryHackMe walkthrough, created to document my learning journey and share solutions with the community. The writeups include a mix of hints, step-by-step explanations, and final answers to help players who get stuck, while still encouraging independent problem-solving.
Metasploit Introduction Room - An introduction to the main components of the Metasploit Framework.
Overview
- Room URL: https://tryhackme.com/room/metasploitintro
- Difficulty: Easy
- Time to complete: 30
Walkthrough
1. Introduction to Metasploit
No hints needed!
2. Main Components of Metasploit
- What is the name of the code taking advantage of a flaw on the target system?
=> Answer: Exploit
What is the name of the code that runs on the target system to achieve the attacker's goal?
=> Answer: Payload
- What are self-contained payloads called?
=> Answer: Singles
Is "windows/x64/pingback_reverse_tcp" among singles or staged payload?
=> Answer: Singles
3. Msfconsole
- How would you search for a module related to Apache?
=> Answer: search apache
Who provided the auxiliary/scanner/ssh/ssh_login module?
msf6 > use auxiliary/scanner/ssh/ssh_login
msf6 auxiliary(scanner/ssh/ssh_login) > info
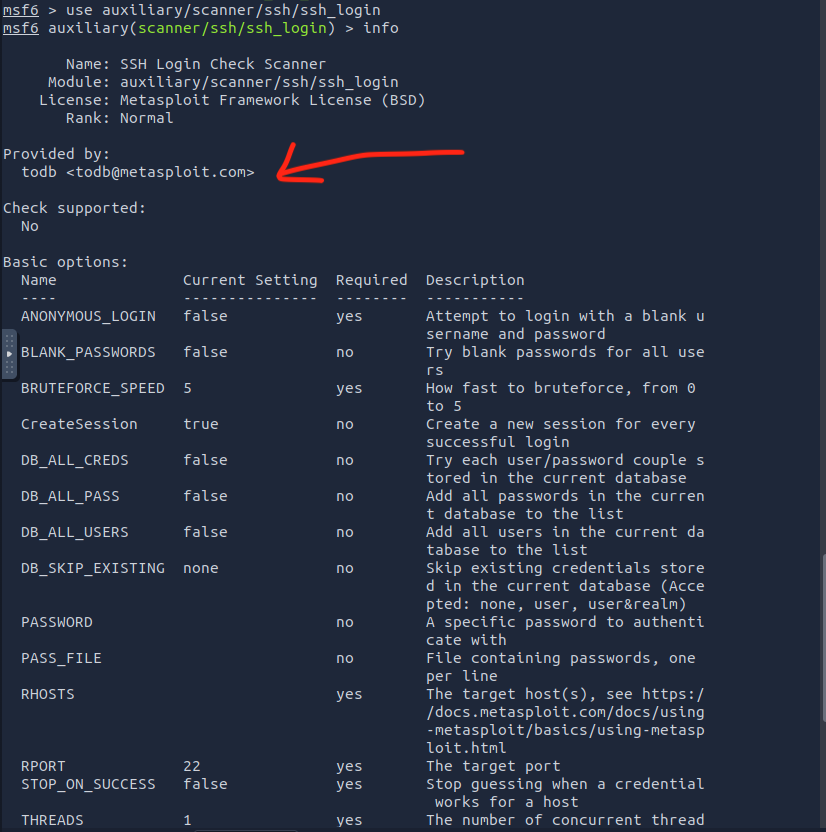
=> Answer: todb
4. Working with modules
- How would you set the LPORT value to 6666?
=> Answer: set LPORT 6666
- How would you set the global value for RHOSTS to 10.10.19.23 ?
=> Answer: setg RHOSTS 10.10.19.23
- What command would you use to clear a set payload?
=> Answer: unset PAYLOAD
- What command do you use to proceed with the exploitation phase?
=> Answer: exploit
5. Summary
No hints needed!